Using Magnet AXIOM to Get Data From Wickr Me
I’m thrilled to announce that with Magnet AXIOM 3.7, we will be supporting the latest version of Wickr Me on iOS for extractions that include the iOS Keychain — something all GrayKey customers should have for every extraction.
Looking for some quick background both about me and our brand-new artifact? I’m Mike Williamson, and I joined the ranks at Magnet Forensics this summer, leaving a 12-year policing career with the Calgary Police Service — the past six years in a digital forensic examiner role. It has been a fascinating, humbling whirlwind of experiences to see things from the software vendor perspective, particularly the tireless effort that gets put in to each and every release.
Trying to Get Data from Wickr Me
Over the last 10 years, we’ve seen digital privacy rights become a focal point of the global conversation. Balancing the individual’s right to privacy with the need to be able to investigate crime has confounded tech companies, the media and governments, and inspired compelling debate from both sides across the world. The significant attention on privacy has inspired a whole new market of privacy-first messaging apps and Wickr Me could easily be the poster child for this type of offering.
Wickr was founded in 2012 out of California and today offers both free and pro versions of its messaging software. Unlike it’s competitors, Wickr doesn’t require a valid phone number to create an account. This makes it an attractive choice, along with some very definitive marketing: use our software to communicate, and you will be protected from every angle. Even ephemerally, whatever that means.
As a forensic examiner during this evolution of security awareness, I certainly did notice a corresponding change in usage patterns. In the past, almost without exception people conducted their texting business out in the open using SMS and maybe an internet chat app or two. Mind you, those chat apps weren’t selected for security reasons but likely sheer convenience (or even because they like a certain app’s emojis).
Nowadays, people absolutely do consider security and whether their data could be getting monetized by a corporate juggernaut. Why? People learn. People who commit crimes are still People, and they hear global news about terrorist investigations and Cambridge Analytica scandals as much as anyone else. The majority realize by now that their phone data may be seized and examined if they are charged with an offence, and so they set out to find the most secure messaging app out there.
So… what academically sound steps are involved in establishing which apps are the most secure?
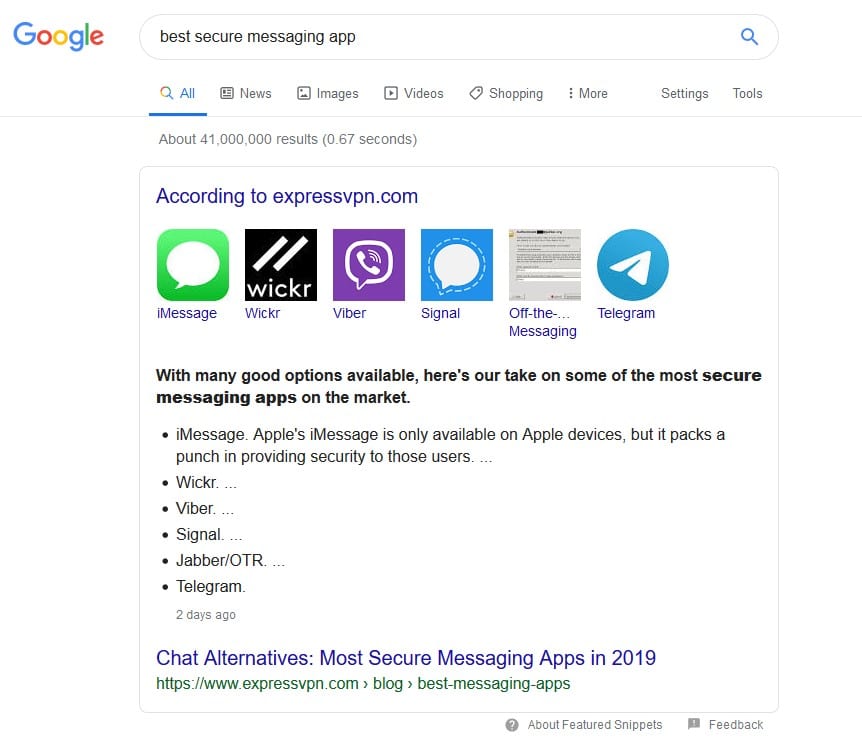
So there you have it— after “extensive research” Google has immediately put Wickr on my radar if I’m interested in the best security available. As a dutiful forensic examiner, striving to stay up on the latest usage trends I know that I should keep an eye out for it on the devices I look at. I’ll be honest— I did encounter it on devices I examined, but I never had much luck decrypting Wickr Me. There were forensic tools out there that said they supported it, but brute forcing was too slow to be useful. If I didn’t have the password – or a lot of patience and time – I was simply out of luck.
“There Must Be Another Way.”
This simple sentiment, coupled with customer requests to support it opened a pandora’s box of research, culminating with what we are releasing in AXIOM 3.7 today: Password-free decryption of Wickr Me on iOS.
As part of my research, I spoke to some in-the-know folks around the #DFIR community, like Binary Hick Josh Hickman, who recently published extensive research about Wickr Me on his blog. Josh also drew my attention to Wickr’s recent open sourcing of some crypto code and a whitepaper, which was quite helpful at certain stages of the process.
With Wickr Me, it turns out there are two paths to crypto-triumph. One, of course being the aforementioned “knowing of the password” which we already discussed. The other path, brought to you today by Magnet AXIOM uses the iOS keychain – a centralized, secure repository for sensitive information like key data. We’ve put together a step by step guide on how this works, conveniently linked in the Wickr Options window, but I also put together a video demonstrating how to use it.
If you’re not already using AXIOM, you can request a free 30-day trial today.
Feel free to reach out to me at mike.williamson@magnetforensics.com or @forensicmike1 on Twitter if you have any questions or feedback.