Following the AirDrop Breadcrumbs with AXIOM
With the recent releases of both AXIOM 3.8 and 3.9, we’ve added additional Mac support to parse the unified log for entries surrounding the use of AirDrop. You can review these AirDrop artifacts on both computer and mobile evidence sources.
Make sure you’ve updated to the latest version of AXIOM so you can make use of these new artifacts today!
Before we get into the weeds of what AirDrop data we are recovering, let’s first review what this service is and why it could be pivotal for both corporate and law enforcement-based investigations. Whether your macOS/iOS case is based on intellectual property theft from an organization and identifying how that data was exfilled, or a criminal investigation tracking contraband on devices, AirDrop should be investigated as a potential source of how that data was moved.
What is AirDrop?
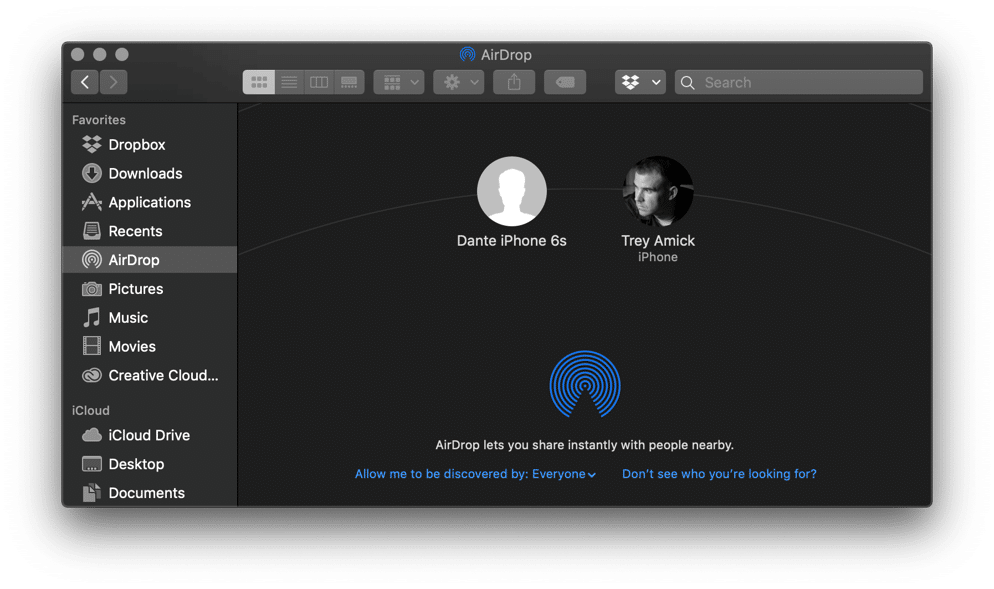
Originally released with Mac OS X Lion (10.7, July 2011) and iOS 7 (September 2013), the AirDrop service creates an ad-hoc network or connection between two devices utilizing both Wi-Fi and Bluetooth. Using AirDrop allows users to transfer files ranging from voice memos, locations, pictures, and videos to full application DMG files—which is ideal since there is not a cap on file size for AirDrop transfers. As we can see below, I have the AirDrop service open on my Mac with the discoverability set to everyone so both contacts and non-contacts alike can share files with me.
AXIOM’s AirDrop Artifacts
As of AXIOM 3.9, there are five AirDrop artifacts for examiners to review when working macOS or iOS investigations. These artifacts include:
AirDrop Background Activity
The AirDrop background activity artifact provides examiners a snapshot of any activity surrounding the AirDrop service found on the system, including but not limited to:
- Scanning mode changes of the device
- When ports are enabled for use
- AirDrop connections being made
- When Finder exited AirDrop, and more
This is more of a secondary artifact which has been designed to flag information we’ve analyzed from the unified logs during processing, so keep in mind some of this information will also be found in more narrowly focused artifacts, such as the AirDrop Discoverability artifact. The details panel for background activity will yield the log details as well as a timestamp for the log entry. It’s also important to note that the timestamp is UTC (yyyy-mm-dd).
AirDrop Discoverability
As the name implies, this artifact allows examiners to see when the Mac or iOS device changed their discoverability mode for potential use of the AirDrop service. There are three modes:
- Everyone, which allows both contacts and strangers to share files with the device
- Contacts Only
- Off
As the AirDrop service periodically resets, you will see status toggles (e.g. Off followed Everyone) within one second of each other. Those are background system activities that are not user induced, however there are actual user-produced mode changes that are buried in the midst of system activity. In an effort to make sure no evidence is missed during an investigation, we’ve kept suspected system activity in the artifact.
AirDrop Incoming Transfers
The Incoming Transfers artifact provides information usually critical to an investigation, such as what data the device received and from where. We’ve included the item type, whether it be an image file or a zip-archive, however if Apple doesn’t have a friendly name for the file type, examiners may see names like “dyn.ah62d4rv4ge80nqbv”.
AXIOM will also display if the incoming transfer had more than one file attached to it as well as the destination folder of the data. Typically, the data gets transferred to the downloads folder or Photos application, or on iOS to the camera roll.
Additionally AXIOM will provide the sender’s name and the device that initiated the transfer, which can be quite useful if you’re working to identify additional persons of interest for your investigation. We’ve also added a field for “Sender is Me” if the sender is logged in under the same account as the recipient.
With this artifact we’ve also included a snippet from the unified log for examiners to review. This transaction log will validate information we’ve processed for this artifact. Utilizing the first and last lines of the log for this event is how AXIOM coordinates the start and end times of each AirDrop Incoming Transfer. As with the other AirDrop artifacts that have timestamps, the Incoming Transfers artifact times are also UTC. If an AirDrop transfer has more than one file attached to it, it will produce a separate Incoming Transfer artifact hit for each file, however examiners can utilize the transaction log to identify and correlate those entries when examining the evidence.
AirDrop Outgoing Transfers
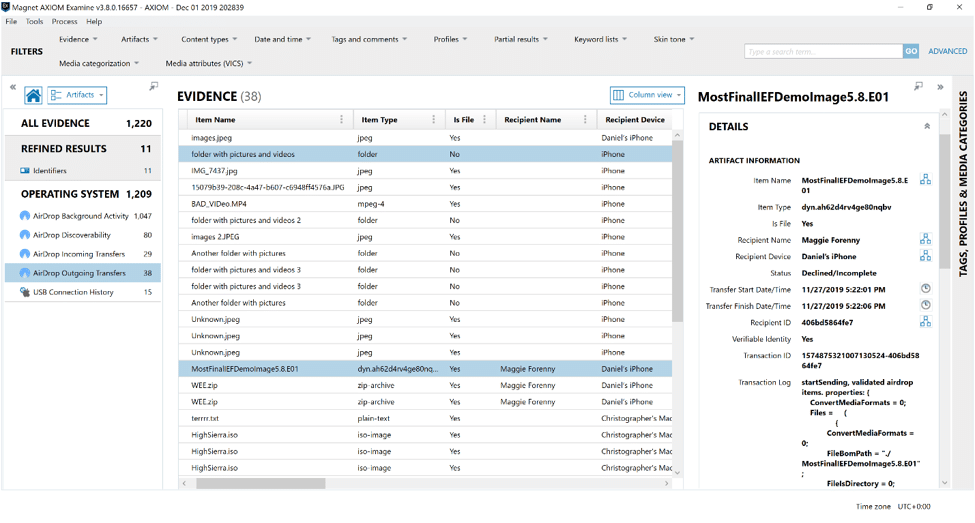
Since most investigations need to identify the files being moved, either for fraudulent means or for distribution of potential contraband, it’s important to identify the details of what’s being shared. While many details of this artifact are similar to the above-mentioned Incoming Transfers artifact, it’s important to understand a little more around the “Status” column of the Outgoing Transfers. Users will either see Accepted or Declined/Incomplete. Unfortunately, there isn’t a way to differentiate between a cancelled, declined, or a timed-out transfer, so they will all be tagged as Declined/Incomplete. As you can see below in the Details panel, the transfer for “MostFinalIEFDemoImage5.8.E01” has been identified as having been Declined/Incomplete.
AirDrop Available Recipients
The Available Recipients artifact provides a listing of recipients the device has found when scanning for potential devices with their AirDrop client running. This artifact provides both a User ID and name that can be used to cross reference to other devices.
These AirDrop artifacts will inevitability help investigators identify how files have moved to and from supported Mac and iOS devices being investigated. Keep in mind, during our testing and research, we were typically only seeing AirDrop artifacts within a week of the event when reviewing the unified logs. For iOS devices, remember you’ll need a file system level image to investigate AirDrop activity.
As I discussed during the extended attributes video released recently, make a habit of reviewing the QuarantineEventsV2.db for AirDrop activity, as well as the extended attributes and spotlight metadata attached to files found on APFS /HFS+ systems. This metadata will help complete the story of your investigation, as it shows if the file was transferred to the system using AirDrop, as well as who transferred it.
Stay tuned, we’ll be adding more artifacts found on the APFS file system soon! If there are artifacts you’d like to see supported in AXIOM or if you have any questions, please don’t hesitate to reach out to me at trey.amick@magnetforensics.com.