
Working With Dell Data Protection Encryption (DDPE) in AXIOM Cyber
DDPE is a file-based encryption method commonly used by businesses to help protect their IP and corporate knowledge. But sometimes the tools that have been put in place to protect our data can actually become roadblocks in our forensic investigations.
Data encryption used to make the content of files inaccessible to unauthorized users is commonly relied on by many corporations for data protection compliance and security. But when the need arises to conduct a forensic investigation for potential IP theft or to support eDiscovery preservations—that file encryption can become a barrier or even a dead end in the investigation.
To help ensure data protection doesn’t stand in the way of your forensic investigations, we have added support for Dell Data Protection Encryption (DDPE) right into Magnet AXIOM Cyber.
What is DDPE?
As a file-based encryption method, DDPE is applied to each individual file on a system, meaning that any file moved from the original device to external media or cloud storage services will retain the encryption. This is great for protecting the corporate knowledge from unauthorized users but can add delays and challenges for forensic investigations.
DDPE Workflow in AXIOM Cyber
With the addition of support for DDPE, you can decrypt DDPE files right in AXIOM Cyber, preserving the forensic integrity of the evidence and mitigating added steps in the decryption process.
Knowing that the business being investigated uses DDPE, the examiner can approach the DDPE administrator who can provide the necessary credentials to be entered into AXIOM Cyber via a bin recovery file and password.
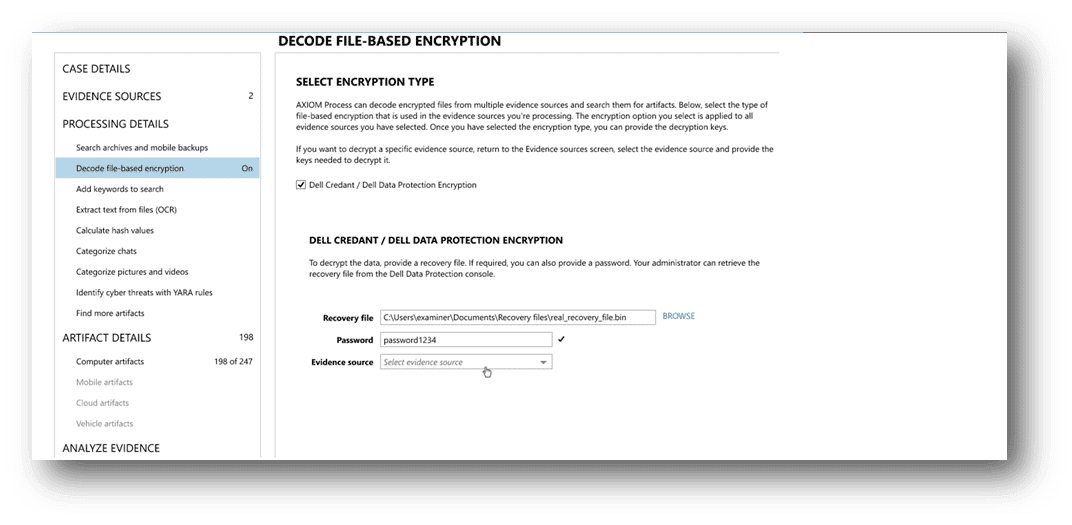
The examiner can then scan each folder to ID any forensic image to identify DDPE encrypted files. Once identified, AXIOM Cyber creates a second image of the decrypted results, which can be investigated or exported. The second image contains just the decrypted evidence with a full file structure and maintains the forensic integrity of the original image while still allowing the examiner to investigate the content of the files.
With the evidence decrypted, it can be loaded into the artifact engine of AXIOM Cyber to leverage the powerful analytical capabilities to quickly and easily surface the evidence that is relevant to you case. AXIOM Cyber also provides data visualizations, so you can intuitively interpret, understand, and tell the story of your digital evidence.
The Process Without DDPE Support
Without support for DDP encrypted files, the process to decrypt and examine data becomes considerably more involved, requiring an examiner to:
- Contact the local DDPE admin to make arrangements to have the data decrypted
- Export the encrypted evidence into a logical evidence container
- Mount the container to export the encrypted files
- Decrypt the files locally or potentially on the administrator’s system
- Export the files back into a logical evidence container
- Reintroduce the decrypted files
The numerous manual touch points in this process are not only cumbersome but also add unnecessary time to acquiring the evidence. Exporting data out of AXIOM Cyber and transferring it to other machines also introduces additional systems and tools accessing potentially sensitive data which could unnecessarily expose the content or compromise the forensic integrity of the evidence.
Get Magnet AXIOM Cyber Today!
To checkout this feature in AXIOM Cyber, update to the latest version or request a free trial.