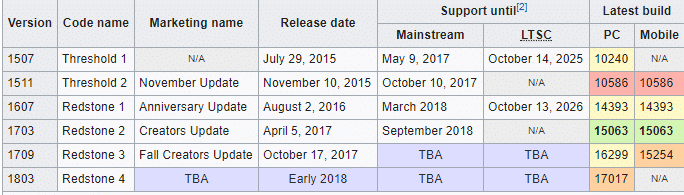What “the Last Version of Windows” Means for Digital Forensics
In January, we released the AXIOM Wordlist Generator free tool and described in our white paper the changes to the Microsoft® Windows® 10 login workflow that affected password cracking practices.
The login workflow was far from the only change in this anniversary update, however. In this blog, Training Director Jamey Tubbs describes other Windows operating system changes that could affect your forensic examinations.
In 2015, Microsoft announced that Windows 10 will be the last operating system they produced:
With this announcement, it appeared that Microsoft would be taking a page from Apple and OSX on how it does updates. This could be a good thing for examiners…or it could be a bad thing.
Microsoft announced it will be releasing two major updates a year and has been naming them YYMM, as Wikipedia details:
Perhaps most importantly to forensic investigations, when Microsoft updates Windows, file locations and registry keys move or change, and new registry keys are created.
What Happens During a Win 10 Upgrade?
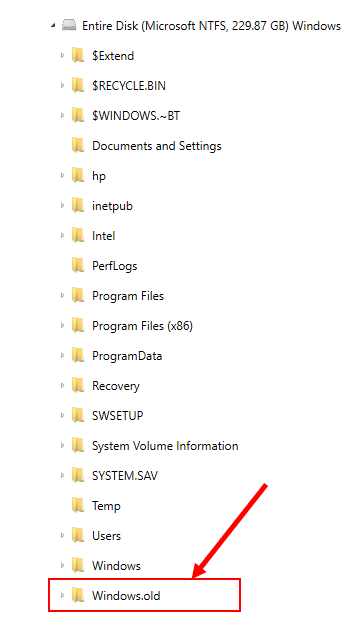
The folder C:\Windows.old is created, which contains all the files and data from your previous Windows installation. It can be used to restore your system to the old version of Windows, should something go wrong with the new version. Windows will automatically delete the Windows.old folder to free up space if the computer runs out of room or after a specific time frame.
In addition, new registry hives are created and artifacts, such as the operating system install date, are changed to reflect the upgrade date and time. If the Windows.old folder exists in your evidence (see the figure below), typical artifacts, such as previously connected USB devices, will be located in that folder. AXIOM will bring these artifacts out and the source will be the Windows.old folder:
For example, in the evidence file depicted navigating to the Artifact Explorer, the Windows\Windows\System32\config\SYSTEM hive only shows the operating system, USB devices, and other artifacts within the current Windows folder. You can see only one USB storage device, a PNY USB 2.0 FD USB Device:
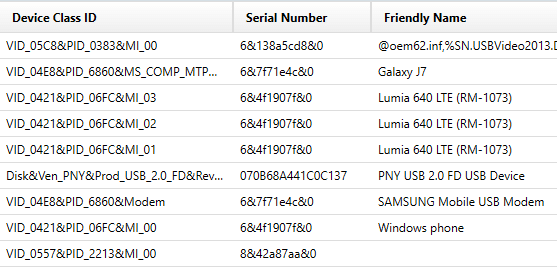
If, however, you look at the Windows.old SYSTEM hive, you would see that a Western Digital 07TECT External USB Device was also present at one time, even though it was not present in the new SYSTEM hive after the update/upgrade:
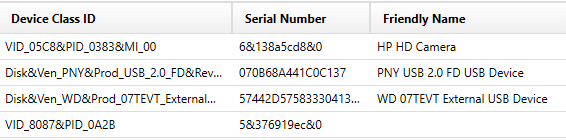
Examine the figure below for details about the Western Digital 07TECT External USB Device, taking note that the source location is the Windows.old folder:
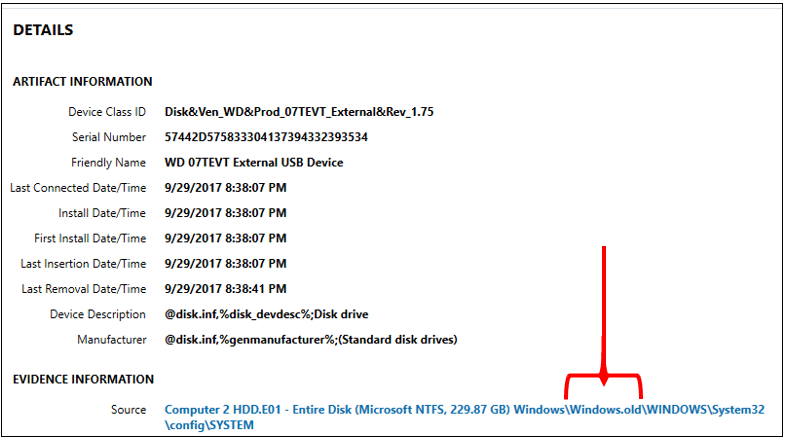
The takeaway from this is: if the Windows.old folder is present, AXIOM will process it. However, if the Windows.old folder no longer exists, the registry may still contain information about USB devices that were connected at one time, and that are no longer present since the Windows.old was deleted.
It’s imperative for examiners to look at both the existing windows registry artifacts as well as the Windows.old registry artifacts from the operating system artifacts found by AXIOM.
Current Install Build Number
Now that we’ve discussed Microsoft’s Windows update rollout plan, you may see how important it is to find the build number on the suspect computer. That way, when you’re investigating, you can make sense of some of the findings you discover.
The Current Install Build Number can be found in the following registry location:
SOFTWARE\Microsoft\Windows NT\CurrentVersion\CurrentBuildNumber
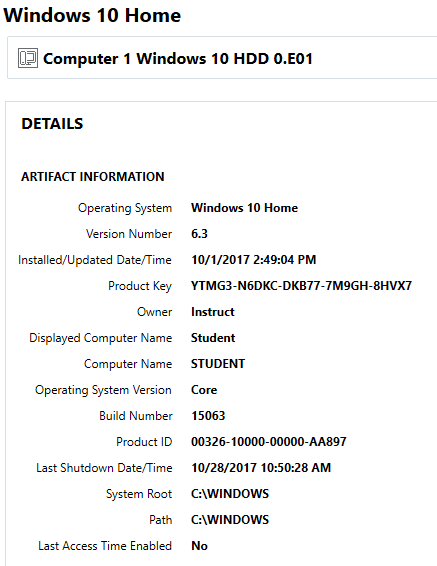
This registry key will reflect the current version of Windows 10. In the picture below, you can see the ASCII value 15063, which is Windows 10, Version 1703. This is important to know, as different versions of Windows 10 have different features, registry keys, etc.
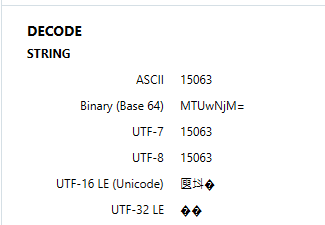
This same information can be located within Artifacts -> Operating System, Operating System Information.

Current Install Date/Time
Do you want to know when the Windows Current Install Date/Time is? Of course you do. But is what Windows tells you is the install date and time accurate to what you think it is?
The install date and time key is located in the following hive:
SOFTWARE\Microsoft\Windows NT\CurrentVersion\InstallTime
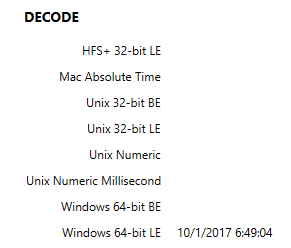
This registry key will tell you when the current version of Windows 10 was installed. In the figure below, you can see the date/time stamp of 10/1/2017 06:49:04. But, is this really the date and time of the original installation?
Previous Installation Dates and Times
Previous installation dates and times can be found in the following hive: SYSTEM\Setup\Source OS (Updated on MM/DD/YYYY HH:MM:SS)
These registry keys will tell you when the operating system was upgraded FROM and the date and time it took place. In the figure below, you can see the registry keys are easily identifiable:
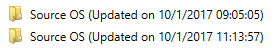
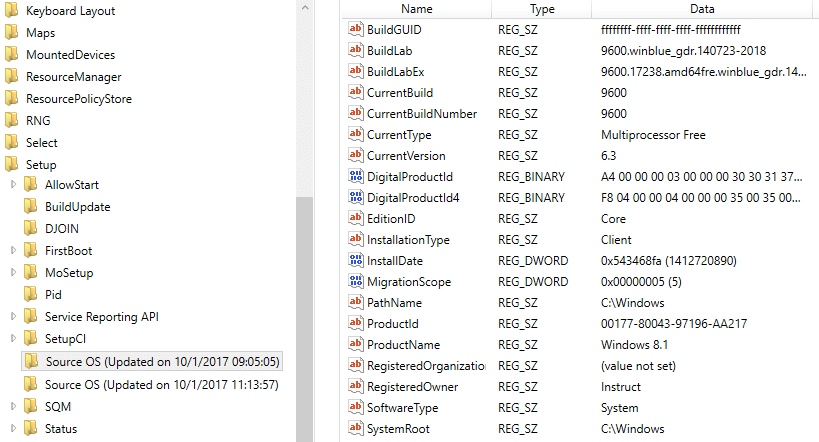
In the figure below, you can see the registry key Source OS (Updated on 10/1/2017 09:05:05). Within this key, you can see the ProductName key has the value Windows 8.1.
However, we do not know what the ORIGINAL install date for this computer was. To locate that, we have to look at the Security Account Manager (SAM) file again. Navigate to the SAM file, SAM\Domains\Account, and click on the F value.
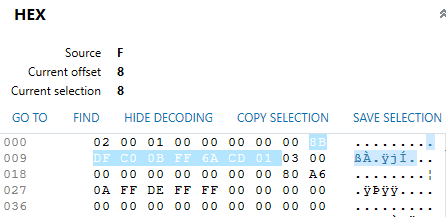
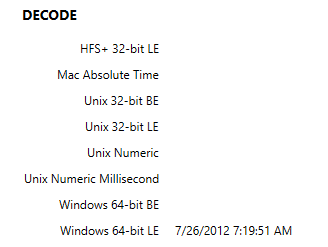
Highlight bytes 8 through 15, as seen in the figure below, then view the Decode as Windows 64-bit LE. You will see the date of the last login. Although for users, this value would be the last login in the SAM\Domains\Account, it reflects the first and last time the “System” logged into the account during initial setup of the Operating System.
Understanding Microsoft’s rollout plan, versioning scheme, and how to find install date/time stamps offers you the ability to understand your findings in terms of each version’s features, registry keys, and other differences. As such, it offers a gateway to finding potential sources and locations of other evidence, such as previously connected USB drives.
Questions? Please email jamey.tubbs@magnetforensics.com!