TrueBot Malware: What It Is and How to Hunt It
This is a post authored by Matt Suiche (Director, Memory, IR & R&D).
The Cybersecurity and Infrastructure Security Agency (CISA) & partners recently released a cybersecurity advisory saying that multiple threat actors are using new TrueBot malware variants against organizations in the United States and Canada with the aim of collecting and exfiltrating data.
We covered how to hunt for web shells in memory in our blogpost “Hunting “Volt Typhoon” State-Sponsored Actor in Memory With Magnet AXIOM Cyber.” In this post, we will dive into how we can achieve the same goal using the YARA rules published in the joint advisory.
What is TrueBot Malware?
TrueBot malware is a known malware used for data exfiltration which has been used by infamous groups such as CL0P ransomware group. Previous versions of TrueBot were delivered through a malicious phishing attachment. This new version leverages a remote code execution vulnerability in the Netwrix Auditor Application (CVE-2022-31199) to gain initial access to the network.
Hunting TrueBot
Like the YARA rules written for hunting “Volt Typhoon”—which were designed for physical files—the YARA rules for hunting TrueBot include conditions specific to their “on-disk” attributes such as “filesize”.
Multiple domain names have been shared as the indicators of compromise (IOCs) which also allows us to have a memory-only YARA rule specifically for those domain names known to be malicious.
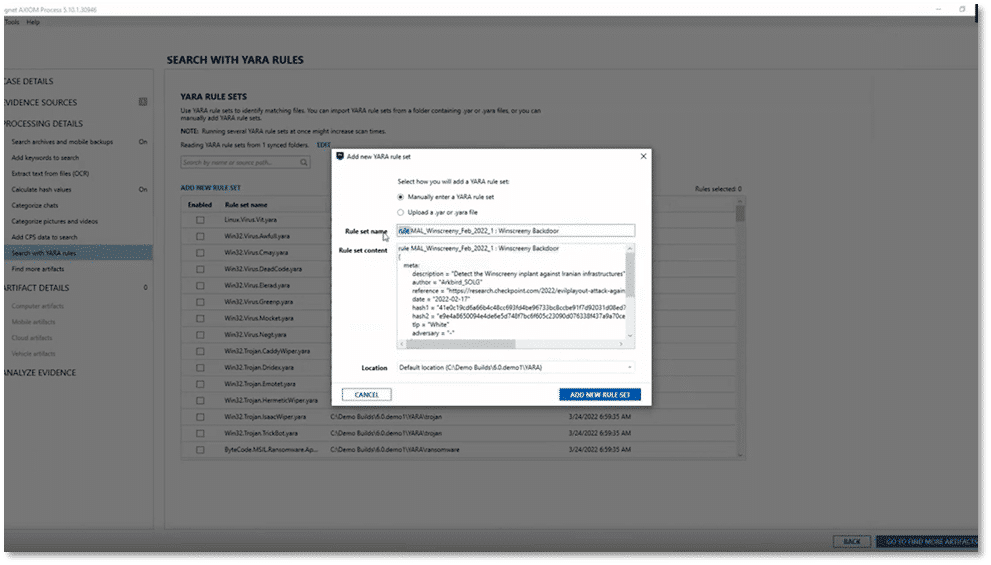
This allows investigators and analysts to scan machines quickly and efficiently in a simple manner. For more information on using YARA rules in AXIOM Cyber check out: YARA Rule Processing in Magnet AXIOM Cyber.
Find Out More About Memory Analysis in AXIOM Cyber
To learn more about the memory analysis capabilities of AXIOM Cyber check out Comae Memory Analysis Capabilities Integrated Into Magnet AXIOM Cyber.
To try the memory analysis capabilities of Comae in AXIOM Cyber for yourself, update to the latest version over at the Customer Portal or request a free trial today!
YARA Rules for Hunting TrueBot Malware
rule TrueBot_Domains_IOC {
meta:
date = "2023-07-08"
description = "Hunts for memory IOCs TRUEBOT."
author = "Matt Suiche - Magnet Forensics"
reference1 = "https://github.com/The-DFIR-Report/Yara-Rules/blob/main/21619/21619.yar"
reference2 = "https://www.ic3.gov/Media/News/2023/230707.pdf"
verdict = "dangerous"
platform = "windows"
strings:
$domain1 = "snowboardspecs.com"
$domain2 = "corporacionhardsoft.com"
$domain3 = "essadonio.com"
$domain4 = "imsagentes.pe"
$domain5 = "hrcbishtek.com"
$domain6 = "ecorfan.org"
$domain7 = "nitutdra.com"
$domain8 = "romidonionhhgtt.com"
$domain9 = "midnigthwaall.com"
$domaina = "dragonetzone.com"
$domainb = "rprotecruuio.com"
$domainc = "nomoresense.com"
$domaind = "ronoliffuinon.com"
$domaine = "bluespiredice.com"
$domainf = "dremmfyttrred.com"
$domaing = "ms-online-store.com"
$domainh = "ber6vjyb.com"
$domaini = "jirostrogud.com"
$domainj = "fuanshizmo.com"
$domaink = "qweastradoc.com"
$domainl = "hiperfdhaus.com"
$domainm = "guerdofest.com"
$domainn = "nefosferta.com"
$domaino = "droogggdhfhf.com"
condition:
any of them
}
rule CISA_10445155_01 : TRUEBOT downloader
{
meta:
Author = "CISA Code & Media Analysis"
Incident = "10445155"
Date = "2023-05-17"
Last_Modified = "20230523_1500"
Actor = "n/a"
Family = "TRUEBOT"
Capabilities = "n/a"
Malware_Type = "downloader"
Tool_Type = "n/a"
Description = "Detects TRUEBOT downloader samples"
SHA256 = "7d75244449fb5c25d8f196a43a6eb9e453652b2185392376e7d44c21bd8431e7"
strings:
$s1 = { 64 72 65 6d 6d 66 79 74 74 72 72 65 64 2e 63 6f 6d }
$s2 = { 4e 73 75 32 4f 64 69 77 6f 64 4f 73 32 }
$s3 = { 59 69 50 75 6d 79 62 6f 73 61 57 69 57 65 78 79 }
$s4 = { 72 65 70 6f 74 73 5f 65 72 72 6f 72 2e 74 78 74 }
$s5 = { 4c 6b 6a 64 73 6c 66 6a 33 32 6f 69 6a 72 66 65 77 67 77 2e 6d 70 34 }
$s6 = { 54 00 72 00 69 00 67 00 67 00 65 00 72 00 31 00 32 }
$s7 = { 54 00 55 00 72 00 66 00 57 00 65 00 73 00 54 00 69 00 66 00 73 00 66 }
condition:
5 of them
}