
Three Ways to Use Remote Endpoint File Lists to Streamline Your Investigations
When you’re faced with a security incident or supporting an internal investigation, quickly obtaining Remote Endpoint File Lists (a full list of all the files and folders present on an endpoint or custodian’s machine) can help you answer key questions.
Specifically, “Was this file still present on the endpoint after the attack?” Or when a client or stakeholder wants to know, “How long will it take to collect and process this case?” These questions can be difficult to answer without a comprehensive list of all the files and folders currently on a machine.
Magnet AXIOM Cyber can automatically (or manually) generate a complete index of the files and folders currently on a remote endpoint – within a few minutes. Now, you can preserve that index and search it to help you during an investigation or for future reference.
In this post, we’ll explore how to use an endpoint file list in your investigation to search for potential evidence or help assess the overall scope of an investigation.
Remote Endpoint File Lists: How Are They Generated?
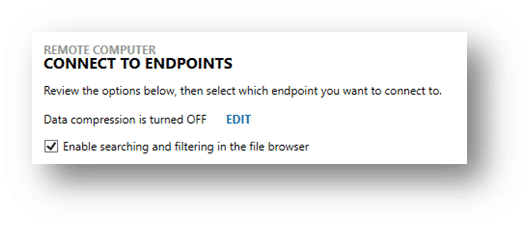
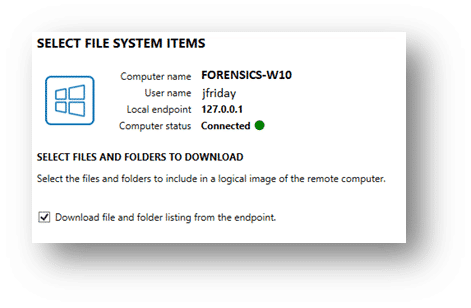
The file listing generates automatically if the “index remote endpoint” feature is enabled in AXIOM Cyber, but a remote file listing can also be generated manually on the targeted collection page.
It’s generated as a comma-separated .txt file, which is not processed post-collection but preserved in the case directory for your reference. For additional context, this index differs from parsing $MFT files in that the index AXIOM Cyber generates captures only the file names and directories currently found on the machine, the date modified, and the file size.
1. Estimate How Long Collection and Processing Will Take
You just received a large case involving several custodians from a stakeholder in your organization’s legal department, and they want to know how quickly you can return a report. How do you estimate how long it’ll take to perform the investigation?
In the context of eDiscovery, during Early Case Assessment (ECA), the file list can be used to quickly estimate collection and processing times by giving you a broad understanding of all files currently on a custodian’s machine and their respective file sizes.
2. Search for a File to Perform a Targeted Collection
For internal investigations or incident response, the presence of a file (or several files) can be quickly validated and preserved prior to a targeted collection. Searching the full file and folder list for the file(s) in question can help you pinpoint which end users or endpoints require a deep dive analysis and where to collect data from using Targeted Locations to save you even more time and effort. Queued collections combined with the file listing of 15 endpoints can be collected in under two hours under ideal network conditions.
3. Validate The Presence of a File
In scenarios where you’re being asked to “go back to the well,” a quick peek at the remote endpoint file list can indicate if a file was present on an endpoint, outside of the scope of the initial targeted collection. You can then go back to your stakeholder to advise that the file was present on the machine.
Additional Resources
To learn more about AXIOM Cyber and how it can help simplify your investigations, check out the following resources:
- Accelerate Your Digital Investigations With Timeline in Magnet AXIOM and Magnet AXIOM Cyber
- Standardizing Your Collections With Targeted Location Profiles in AXIOM Cyber
Try AXIOM Cyber today! Request a free trial here.