The Art of Detection: Digital Forensics and Intellectual Property Theft
What Is Intellectual Property (IP)?
Company-owned data, copyrighted work, trademarks, and patents are all forms of intellectual property. Intellectual property rights are designed to protect originators, creators, and inventors. In developing this data, organizational investments in time, effort, and resources foster economic growth through commercializing ideas and creations. Intellectual property generates revenue for the economy through advancements in existing companies, the creation of new industries, and career opportunities. Intellectual property rights are intended to help protect both businesses and consumers. They ensure that organizations are protected, and sensitive data is safe. Organizations need to protect their data from external threats and understand the risks associated with insider theft.
IP Theft Defined
Regarding intellectual property theft, financial losses can be unimaginable to an organization, impacting their bottom line, dropping team morale, and slowing down the trajectory toward successful profitability. Intellectual property theft from an organization results from the unauthorized use of someone else’s information. IP theft violates the original owner’s rights and can result in legal ramifications such as fines, damages, and, in some cases, criminal charges.
Applying Digital Forensics
How can digital forensic professionals help an organization investigate IP theft? Identifying if the threat to the organization is external, internal, or both is an excellent first step. As with any digital investigation, examiners need to fully understand the scope of the case by identifying key custodians involved in the development of intellectual property, including creators, inventors, or other stakeholders. All involved custodians are potential sources of information that can help steer the case and best prepare an examiner for their next step, identifying data sources.It is common to find multiple sources of data for each custodian involved. Take a moment to quickly assess the number of electronics you own or operate, including company owned assets, and how much data you generate daily. The numbers are staggering, “On average, U.S. households now have a total of 22 connected devices.” The custodians and digital forensic consultants are responsible for working with legal teams to identify and provide an inventory of all relevant data sources, such as mobile phones, laptops, and cloud platforms, to name a few of the most pertinent.
All data associated with the investigation must be acquired in a forensically sound manner, without changing their properties. A simple screenshot or device screen recording will not suffice in today’s digital age, nor will it meet the standards of the legal system. The digital forensics professionals involved in the litigation must now rely on their training and expertise to choose the correct forensics tools for data collection. Deciding on the right tool can be an extensive and sometimes debatable process, as all tools are not created equal. One acquisition tool may do a fantastic job of collecting logical data from a mobile device. Another is best-in-class for collecting all the data, including ephemeral or encrypted third-party applications containing business correspondence – and the data needed to move forward with the legal review process.
For instance, it is common for business executives to use mobile applications designed with additional security to conduct business correspondence. However, you might be surprised to learn that most of today’s standard data acquisition tools cannot collect this type of information in a forensically sound manner, regardless of how relevant it is to an investigation. Multiple barriers to collecting this type of information include application encryption and additional hardware security.
Messaging platforms may contain proof of data theft. According to this survey, texting is the most relevant and preferred way for people to communicate, with SMS (short message service) clearly outpacing phone calls, emails, and other messaging tools. If the investigation shows that data exfiltration occurred because of an insider threat, but your findings show little movement of data originating from the organization’s network to removable storage or cloud platforms, mobile device forensics is a great avenue to pursue. Everyone in an organization has a mobile device, either company-owned or BYOD (Bring Your Own Device).
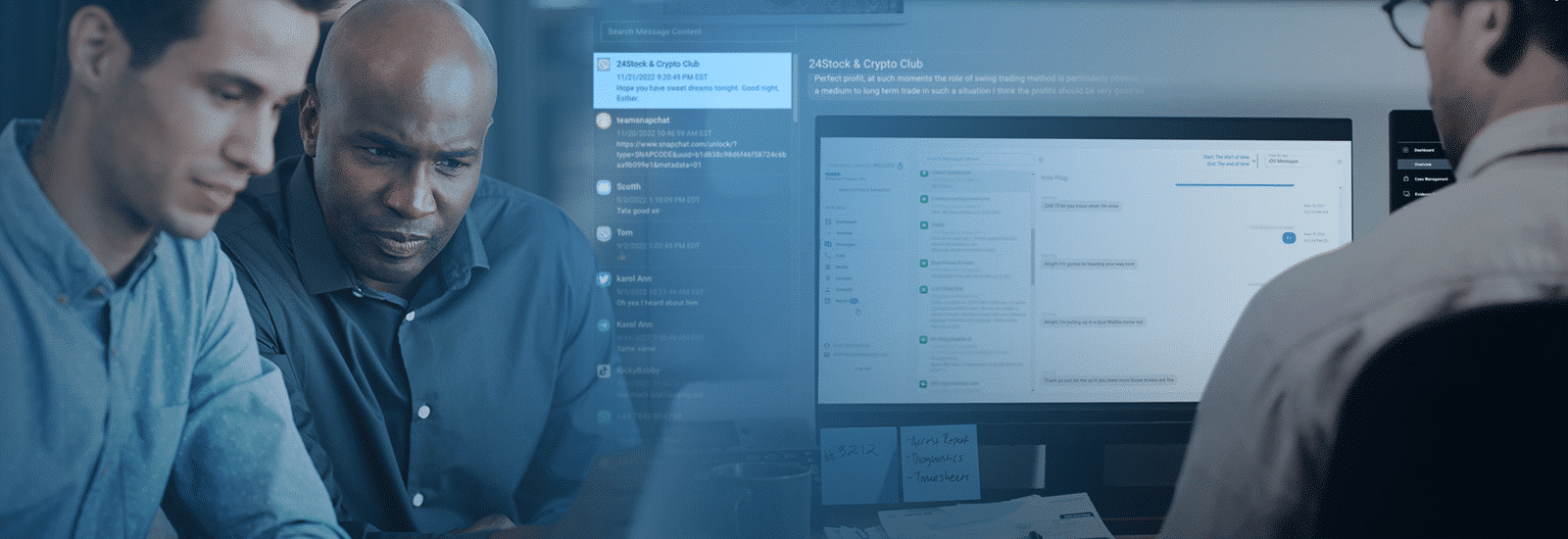
How Magnet Verakey and Magnet Review Can Help
Verakey and Review can help collect and analyze mobile device digital evidence relevant to an intellectual property theft case through tools and techniques built from the ground up. Most collection tools only acquire a small subset of the data undoubtedly lack valuable information and are not in use with Verakey. Suppose you need the full picture and a completed dataset of a custodian’s mobile device, whether company-owned or BYOD. With Verakey and Review, investigators can acquire, preserve, and analyze the contents of the full file system.
Verakey users can quickly determine key elements of IP theft through all the categories available within Review. Once tagged as important, users can quickly generate reports of their findings and present them to key stakeholders.
Best Next Steps
The case is not over because data has been successfully acquired and analyzed. According to this article, businesses must remain diligent and protect their digital assets from data theft by reviewing their security policies and enabling additional layers of protection. Lastly, company employees saving data on their devices may sometimes act nefariously. Ongoing company-wide training offered by industry experts can help ensure that organizations have the tools to mitigate the risk of damage, like controlling access to sensitive data and having an incident response plan.
Sources:
https://leadferno.com/blog/survey-texting-is-the-preferred-way-to-communicate
https://www.business.com/articles/protect-your-business-from-a-data-breach/