
ShimCache vs AmCache: Key Windows Forensic Artifacts
In digital forensics, Windows operating systems leave behind a wealth of forensic artifacts that can be invaluable in investigations. Among the key artifacts are ShimCache (Application Compatibility Cache) and AmCache (Application Activity Cache).
These artifacts can provide valuable insights into program execution and file system interaction, often essential in piecing together an event timeline or detecting unauthorized activity.
In this blog, we’ll explore the forensic significance of ShimCache and AmCache, their locations, how entries are populated, their investigative value, and how they can be used in real-world cases.
What is ShimCache?
ShimCache, also known as the Application Compatibility Cache, is a feature in Windows designed to maintain compatibility for applications running on newer operating systems. It tracks the execution of applications, whether they were executed recently or in the past. ShimCache is part of the AppCompat framework, which Windows uses to ensure compatibility with older applications.
Location and structure
ShimCache entries are stored in the Windows Registry at the following location:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\AppCompatCache
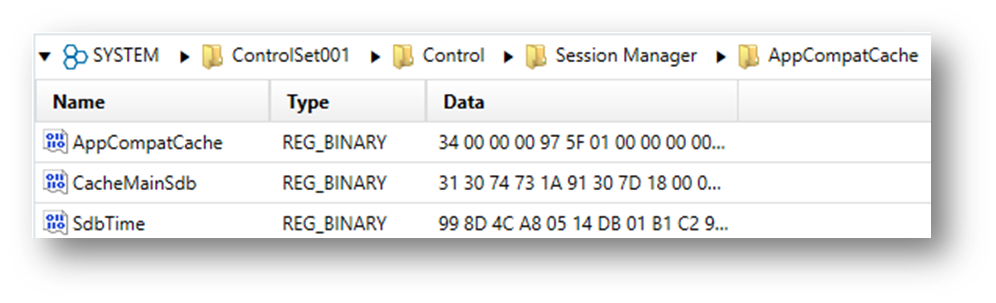
On older systems like Windows XP and 2003, ShimCache is located in the following Registry path:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\AppCompatibility

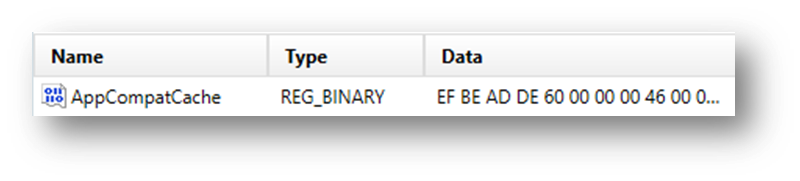
ShimCache stores information in binary format, and tools like Axiom and Axiom Cyber are needed to parse and analyze this data.
How ShimCache entries are populated
Entries in ShimCache are populated when an executable is run on the system. The cache stores metadata such as:
- File path of the executable
- Last modification time of the file (not the execution time–shown below in the “Key Last Updated Date/Time” field)
- Execution Flag **This was deprecated after Windows XP
From an XP Image, we can see what data was contained:
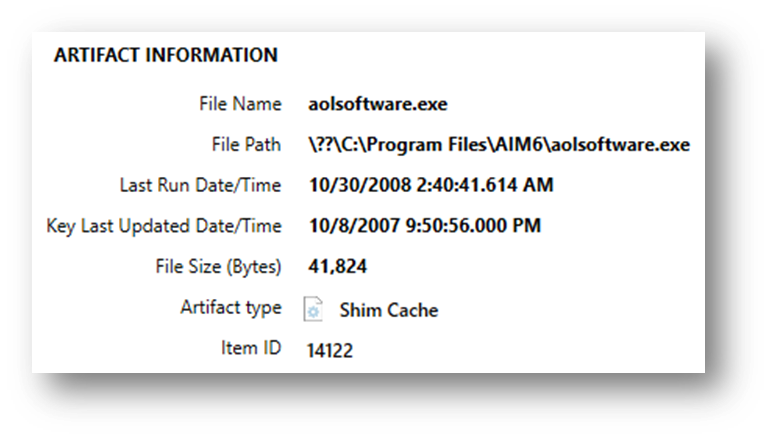
From a Windows 11 image, we see what is now contained:
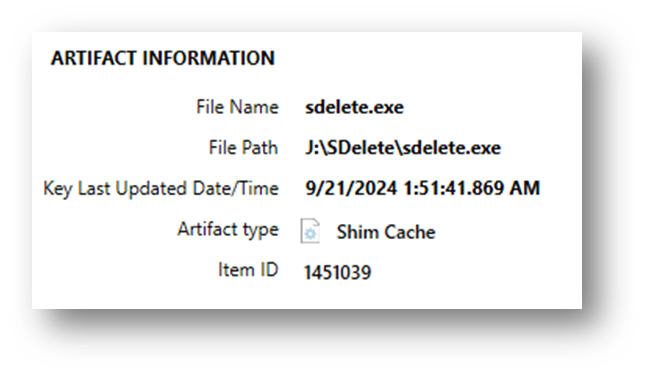
It is essential to note that ShimCache does not always capture actual execution–some entries may represent app.
ShimCache Forensics
ShimCache forensics are significant in forensic investigations for tracking potential program execution. It offers a snapshot of executables present on the system at the time of its last shutdown or reboot, making it useful in timeline construction. While it does not provide direct execution timestamps, it can corroborate activity observed in other forensic artifacts such as Prefetch files, Windows Event Logs, and AmCache.
In Windows systems, whenever a program is run or loaded into memory, its metadata–file path and last modified time–may be cached in ShimCache, and the key is written when the system is shutting down. The last modified time is not altered by execution but is updated if the file itself is modified (such as through updates or changes to the binary).
The last modified time in ShimCache can have forensic significance in several key ways:
- Corroboration of file modification: The last modified time in ShimCache can help establish whether a particular executable was tampered with or updated before being loaded into memory or executed. For example, if malware or a suspicious program was installed and modified before execution, ShimCache can help reveal when this modification occurred. Investigators can compare this with other timestamps (such as file creation or access times from the file system) to determine when changes were made.
- Timeline construction: In the absence of an execution flag (for versions after Windows XP), the last modified time becomes an essential data point to help build a timeline of activity. While it doesn’t tell you exactly when a program was executed, it can indicate that it existed and was modified before its appearance in ShimCache. This can be especially useful when matching ShimCache data with other logs or forensic artifacts, such as Prefetch files or Event Logs.
- Detecting staged files: If an executable appears in ShimCache with a last modified time that predates an incident, this could suggest that the file was staged on the system before being executed or loaded. This is particularly useful in malware or insider threat investigations, where files might be planted on a system for later execution. The presence of a last modified time prior to suspicious activity can indicate that the executable was prepared in advance.
- Identifying backdated files: Attackers sometimes manipulate the timestamps of malicious files to make them appear older or unrelated to an incident. The last modified time in ShimCache, when compared with other timestamps (such as the file system or Event Logs), can help investigators detect potential timestamp tampering. If there is a mismatch between the last modified time recorded in ShimCache and the same file’s metadata in the file system, it may indicate that the file’s timestamp was altered.
- Correlating with updates or patches: In legitimate software scenarios, the last modified time can help verify whether specific applications were updated or patched before being run. For example, an organization may want to verify if a program was modified (e.g., through an update or patch) before a security incident occurred. The last modified time can help distinguish between different versions of the same software that may have been executed over time.
What is AmCache?
AmCache (Application Activity Cache) is a forensic artifact in Windows operating systems, first introduced with Windows 7 but fully implemented in Windows 8 and higher, as we see below. AmCache tracks metadata about executables and other files that have been run on (or interacted with) the system. AmCache serves as part of Windows’ Application Compatibility Framework (AppCompat), which helps ensure programs run smoothly on the system by recording information about program execution.
Location and structure
AmCache data is stored in the following Registry key:
C:\Windows\AppCompat\Programs\Amcache.hve
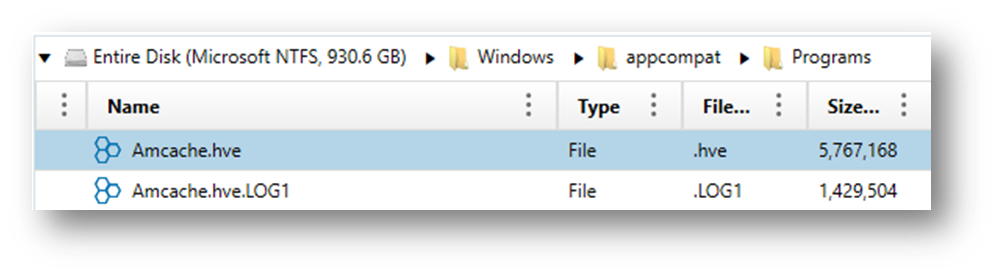
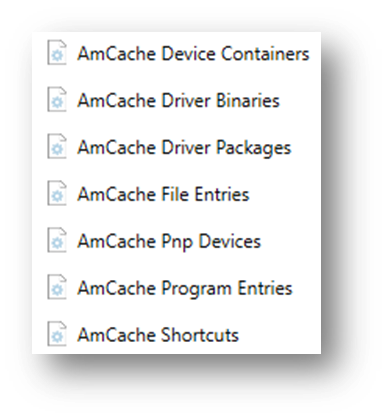
This hive file can be found on disk and parsed using specialized forensic tools like Axiom and Axiom Cyber. Here we see in Axiom Amcache.hve broken down into several categories:
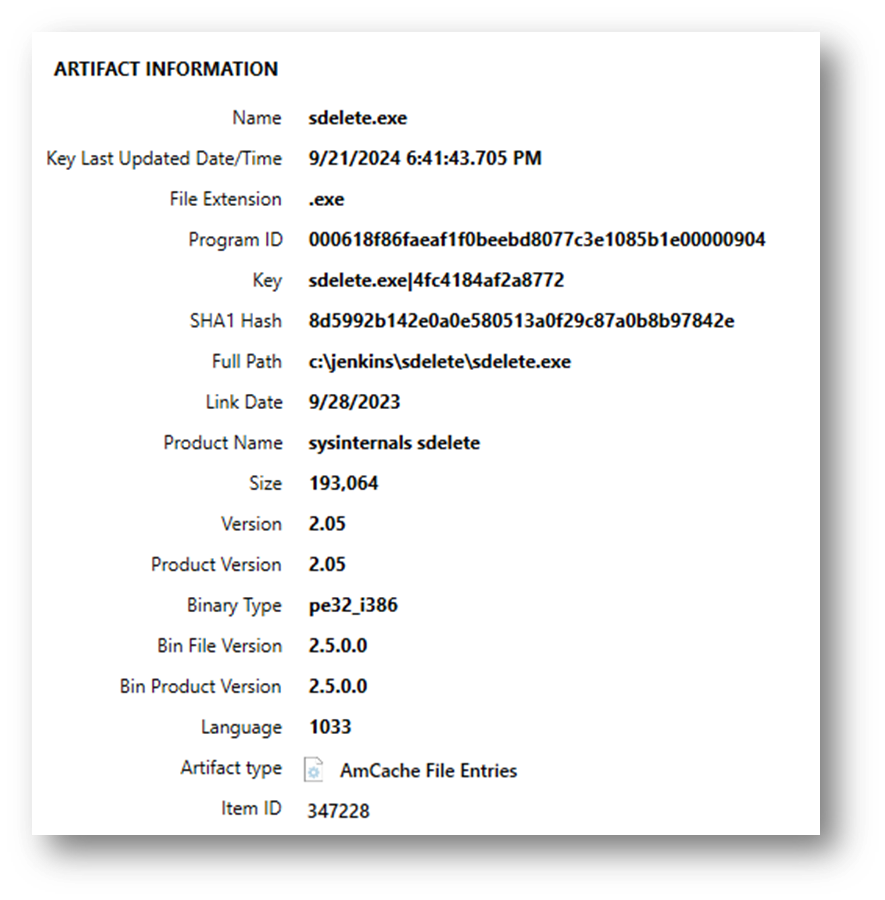
The AmCache hive contains detailed information about executables, including:
- Full path to the executable
- SHA1 hash of the file
- File size
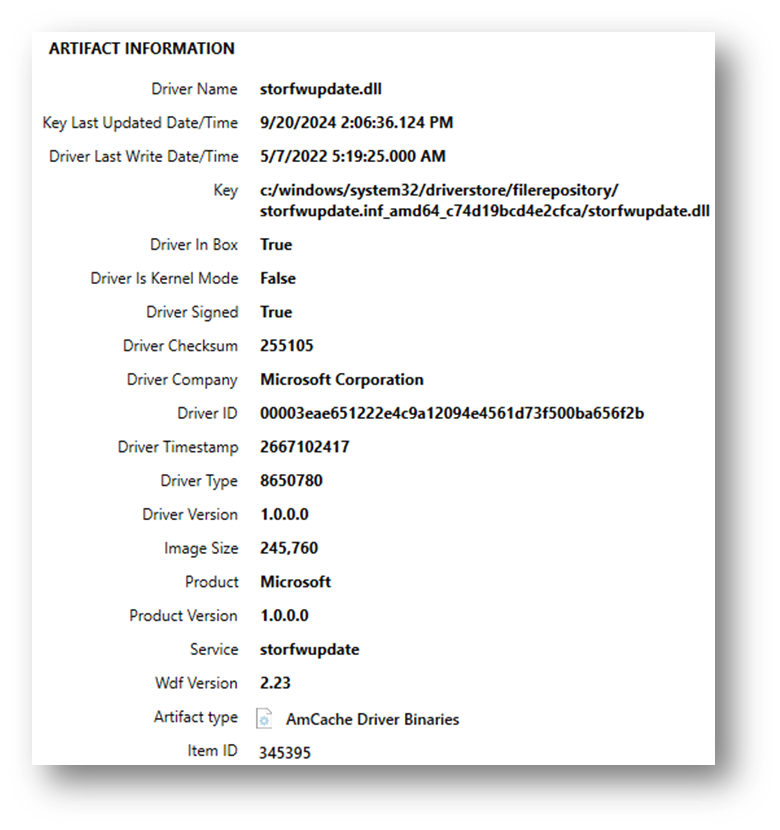
Additionally, AmCache stores information about dynamic-link libraries (DLLs) loaded by the system, which can provide even deeper insight into program activity. Here is one example entry:
Forensic significance of AmCache
AmCache is one of the most significant and detailed artifacts available to forensic investigators on modern Windows systems. Introduced in Windows 8, AmCache provides a wealth of information about executables and DLLs that interact with the system, recording key metadata which helps investigators piece together a forensic timeline of program activity. Unlike ShimCache, which captures metadata at shutdown, AmCache provides live data and tracks when files were first executed, making it a more reliable indicator of execution.
AmCache tracks a range of important metadata, including the full path to the executable, file size, and critically, SHA-1 file hashes. This combination of data makes AmCache a powerful resource for determining program execution, identifying malicious files, and corroborating events with other forensic artifacts.
Forensic significance of SHA-1 file hash
One of the most powerful features of AmCache is its ability to record the SHA-1 file hash of executables and DLLs. A file hash is a unique, cryptographic representation of the contents of a file, and the SHA-1 algorithm generates a 160-bit hash value that can be used to verify a file’s integrity. The forensic significance of SHA-1 hashes in AmCache cannot be overstated, as they serve several critical purposes:
- Verifying file integrity:
The SHA-1 hash allows investigators to verify the integrity of the file by comparing the hash stored in AmCache with the hash of the same file on disk. If the hashes match, it confirms the file has not been tampered with since it was first executed. If there is a discrepancy between the two hashes, this could indicate the file was modified after its initial execution, which might suggest malware tampering or other malicious activity. - Identifying malware variants:
One of the most powerful uses of the SHA-1 hash is in malware identification. Malware authors often create slightly different versions of the same malware to evade detection by antivirus programs. These versions may have different names, sizes, or even small modifications to their code, but they will generate a unique hash value. Investigators can take the SHA-1 hash from AmCache and search known malware databases (such as VirusTotal) to identify the specific malware variant that was executed. For example, if an investigator finds a suspicious file with an unknown name–but can use the SHA-1 hash to identify it as a known ransomware variant–they can immediately understand the scope of the threat and take appropriate action. - Cross-referencing across systems:
In enterprise environments, attacks may occur across multiple systems. Using the SHA-1 hash from AmCache, investigators can search for other systems that may have encountered the same file, even if it had a different name or was in a different directory. The file hash allows forensic teams to track the spread of malware or unauthorized software across an organization. - Corroborating evidence:
SHA-1 hashes also allow for the correlation of evidence across multiple forensic artifacts. For instance, if a file is found in Prefetch, Event Logs, or in network traffic, and its hash matches the one recorded in AmCache, this corroborates that the file was executed at the same time as recorded in those other artifacts. This multi-artifact corroboration strengthens the forensic timeline and provides a clearer picture of events.
Comparative Overview of ShimCache and AmCache
| ShimCache | AmCache |
|---|---|
| Tracks executable metadata at system shutdown | Tracks executable activity in real time |
| Available on Windows XP and later | Fully available on Windows 8 and later |
| Does not record actual execution time | Last Modification Time of the Key = First execution time (stored in AmCache.hve\Root\File{Volume GUID}\key) |
| Captures file path and modification time | Captures file path, SHA1 hash, file size |
Investigative use case 1: Detecting data exfiltration
Let’s explore how ShimCache and AmCache can be used in a real investigation scenario. Consider an insider threat case where an employee is suspected of exfiltrating sensitive data by executing unauthorized programs to transfer files to an external server.
- Initial investigation: The forensic team acquires an image of the employee’s workstation. One of the first steps is to examine program execution artifacts like ShimCache and AmCache to identify any suspicious executables the user might have run.
- ShimCache analysis: Upon parsing the ShimCache, the investigator finds several entries showing a file transfer utility stored on an external USB drive, indicating the utility was loaded or interacted with the system. However, since ShimCache doesn’t provide execution times, the investigator cannot confirm if the program was executed.
- AmCache analysis: The investigator then turns to the AmCache artifact, which provides a more detailed view. Upon parsing the AmCache, the first execution timestamp of the file transfer utility is found (using the last modification time of the key), along with the SHA1 hash, which the investigator uses to identify the exact version of the program. AmCache also reveals the utility was executed multiple times, with timestamps corresponding to periods where unauthorized data transfers were suspected.
- Corroboration with other artifacts: Using the first execution time, the investigator correlates the data with network logs and confirms that outbound data transfers were made during the same period. Further analysis of Prefetch files and Event Logs provides additional confirmation of the tool’s use.
- Conclusion: The combination of ShimCache and AmCache data, alongside other forensic artifacts, allows the investigator to build a comprehensive timeline of events, showingthe employee used the file transfer utility to exfiltrate data to an external server.
Investigative use case 2: Malware execution
Consider a scenario where law enforcement is investigating a cybercrime case involving ransomware. A suspect’s computer is seized during a raid, and the forensic team needs to determine if the suspect executed the ransomware on their system.
- Initial forensic examination: After acquiring the suspect’s computer, the forensic team analyzes the hard drive for traces of the ransomware’s execution. Given that ransomware is known to modify critical files, examining the program execution artifacts (ShimCache and AmCache) is crucial.
- ShimCache analysis: The ShimCache data reveals the presence of a known ransomware executable that had been loaded onto the system. However, since ShimCache doesn’t show the exact execution times, it only confirmsthe malware existed on the system at some point before shutdown.
- AmCache analysis: Next, the investigators parse the AmCache hive. This reveals the ransomware executable was first executed on a specific date, which coincides with the ransomware attack timeline. The AmCache also includes the SHA1 hash of the executable, which the investigators cross-reference with known ransomware samples in the malware database, confirming the exact variant used.
- Building the case: The investigators correlate this data with other forensic artifacts, such as Prefetch files, Event Logs, and network activity logs, to prove the ransomware was indeed executed. The AmCache data serves as a critical piece of evidence, tying the execution of the malware to the suspect’s system.
- Conclusion: In this law enforcement scenario, ShimCache and AmCache play a vital role in proving the suspect executed the ransomware. AmCache, with its first execution time and file metadata, provides crucial evidence that helps the investigators build a timeline of events, confirming the suspect’s involvement in the cybercrime.
Conclusion
ShimCache and AmCache are two powerful forensic artifacts that provide invaluable insights into program execution on Windows systems. While ShimCache gives a broad view of executables loaded by the system, AmCache provides a detailed and reliable source of first execution data, file metadata, and file integrity (through hashes). Together, these artifacts can help investigators uncover critical evidence in cybercrime, insider threats, and malware investigations. When used alongside other forensic artifacts, they provide a comprehensive picture of file system activity and program execution, which is essential for modern digital forensic investigations.