
Revealing hidden data: Full file system extractions uncovered
The two types of extractions for mobile device investigations are full file system extractions and logical. It’s important to know the difference, since iOS and Android devices in digital forensics have become increasingly important in both law enforcement and corporate investigations.
Mobile device evidence can be critical to the investigations of fraud, intellectual property theft, policy violations, litigation support, insurance investigations, and eDiscovery.
Knowing the critical nature of mobile device information in these cases, it is important to understand the types of extractions available. Full file system and logical extractions have significant differences in what data is extracted from the device.
Logical extractions focus on user data and files that can be accessed through standard interfaces. These include contacts, traditional SMS messaging and limited application data. Full file system extractions are a much more complete extraction of data. They includes file system data that users would not normally be able to access directly: the user-generated data from the logical extraction, system files and much more application data.
In this examination, we extracted data from a test device utilizing Magnet Process Quick Image, which is a logical extraction. We also extracted a full file system extraction using Magnet Verakey. The extractions were then processed into Axiom Cyber 8.0.0.39753.
Let’s look at the overall difference in the amount of extracted data:
Quick (logical) extraction

Full file system extraction

Overall, we can see there is a considerable difference between these two extractions, now let’s focus on a couple of major differences:
Email and Calendar
Logical extraction

Full file system extraction

In this category of artifact, there is a clear delineation between the two extractions. Both were able to extract the Calendar, but only the full file system retrieved any Gmail emails.
For example, in an intellectual property theft investigation, the communications between the employee and outside individual attempting to procure the IP would not have been discovered if the email had not been collected. In a recent case that utilized a full file system extraction and Magnet Axiom to parse the evidence, the employee had been utilizing a separate email from the corporate-provided one. The emails captured from this device provided a timeline of contacts, identified a conspirator, and identified a negotiated price for the stolen IP. Going back to the test data, we can see that an email from Facebook could provide the critical context (and time) that would only be apparent through the extraction of a full file system:

Location
Logical Extraction

Full File System Extraction

Again, we see considerably more categories of artifacts extracted utilizing the full file system extraction.
Location data can be some of the best artifacts to identify and can be applicable across a broad spectrum of investigations. For internal investigations in particular, location data can provide the ability to contradict or affirm an employee’s statement as to their location. For example, this location data point could be critical and/or responsive to the request for information that would not be found in the logical extraction:

Communications
Communications are frequently the most sought-after data that can be extracted from mobile devices. Again, the full file system extraction contained considerably more data:
Logical extraction

Full file system extraction

Communications is another artifact category that can be useful in a variety of investigations. The extent of captured communications in a full file system extraction is significantly greater than the traditional logical extraction. In particular, third-party communication applications (Snapchat, Signal, Facebook Messenger, etc.) are likely only to be captured in the full file system extraction. Communications can set up interactions between co-conspirators, identify a timeline of activities, and even provide images (see example below). In a recent case utilizing a full file system extraction and Magnet Axiom, it was discovered that an employee had responded to a smishing attempt over a third-party communication application. After entering their credentials, it allowed for the employee’s credentials to be compromised. This interaction was only captured as part of the full file system extraction.
Going back to the test data, we can see a Snapchat message located only in the full file system extraction containing a potentially relevant exchange:

Web activity
Another extracted artifact that is of critical interest is the web browser-related activity on the device:
Logical extraction

Full file system extraction

The difference in this case is the depth of the data extracted from the device. The logical does have some web browser activity, the full file system just has significantly more data.
In this example, the device was navigated to the website https://helka.finna.fi/, which was not found in the logical file extraction. The act of navigating to this website could be critical to the data collection and full picture of the investigation. Web history can also be used across many investigations from employee misconduct, incident response, and litigation support. Getting a full picture of activities on a device can only be achieved through a full file system extraction.
The categories “Safari iCloud Devices” and “Safari iCloud Tabs” are two additional groups of artifacts that could provide additional information in this case. Safari iCloud Tabs contains information about tabs that have been opened in the browser and synced to an iCloud account. Synchronized tabs are available to any device that logs in to the iCloud account. Safari iCloud Devices contains information about the devices that are synced to an iCloud account. Each device can access any browser tabs that are synced to the account. A closer examination of these categories could identify evidence that may need to be collected for the investigation, which could include physical devices and/or iCloud accounts.
System information
In this final category, we examine information only tracked by the iOS system and would not be visible to the user. Let’s first examine this data grouped under Operating System and Application usage:
Logical extraction:


For the full file system extraction:

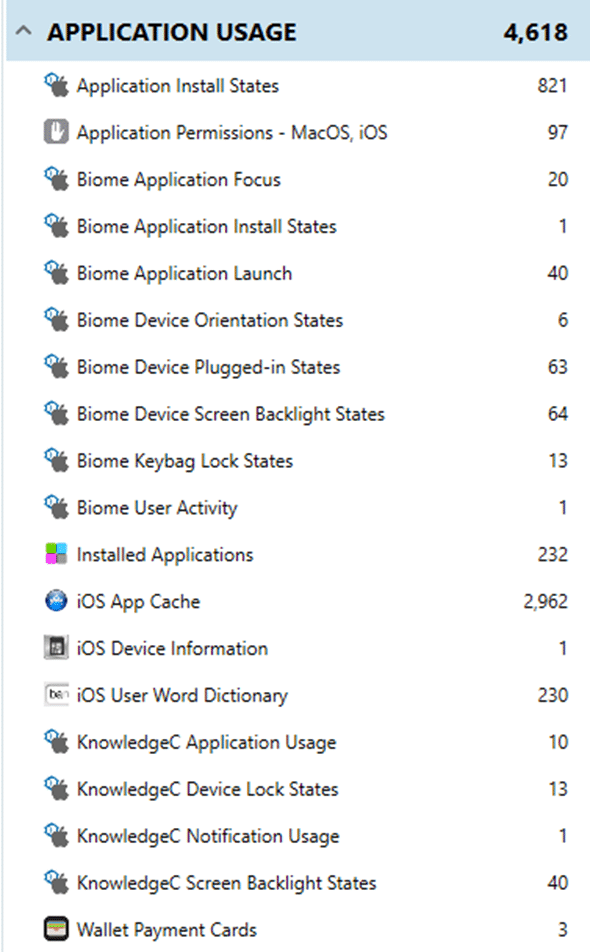
But why would the system information and Application usage be of interest? Here are some artifacts that would only be seen in the full file system extraction:

From the Biome Application Launch artifact, we can see the user launched the MobileSMS application which included the specific date and time. This date and time could be critical to when an event took place in the investigation timeline. Additionally, this system information contains lock and unlock time(s) of the device. This deep-dive information can be critical to investigations such as automotive accidents. Showing that the driver of the vehicle was actively interacting with the device during the time of the accident can be the only item that gives a full picture of what happened and also only available in the full file system extraction.

In recalling back to the critical “Communications” section, the fact that KnowledgeC and Biome data is retrieved in the full file system extraction potentially provides additional communication information. The KnowledgeC data stores a wealth of pattern of life data, and the “AppIntents” storage could contain removed/redacted messages. Biome data (introduced in iOS 16) has multiple locations (AppIntents, SiriIntents and UserActivity) that can store the contents of sent/received messages.
In conclusion, the full file system extraction that is available from iOS devices acquired using Magnet Verakey provides significant advantages over traditional logical extractions. By capturing a more complete acquisition of the entire file system, you can capture data that could be critical to your examination. For this example, email, location, communication, web activity and system information were captured in the Verakey extraction that could contain the piece of information critical to the investigation and/or responsive to the legal/eDiscovery request.
Related Resources
- See how Magnet Verakey was used in four real-world cases in the webinar “Data Uncovered: Revealing Truths in eDiscovery with Magnet Forensics Solutions” with guest speaker Shanon Burgess, Digital Forensic Examiner, at Aperture
- Learn more about Magnet Verakey and request a demo here.