
Remotely (& Covertly) Acquire Mac with Magnet AXIOM Cyber 4.0

If you have Mac endpoints in your environment and need to collect evidence over a network connection, AXIOM Cyber 4.0 is here to help! We officially launched AXIOM Cyber in January with Windows remote acquisition capabilities, AWS S3/EC2 support, Microsoft Teams, Slack, and a whole host of other cloud capabilities, and while customers are loving the Magnet approach to remote acquisitions, we’ve heard the need for reliable macOS support.
In this blog we’ll talk about our macOS remote acquisition capabilities and how we are working around some of the roadblocks that customers have faced when investigating Macs around T2 encryption and System Integrity Protection (SIP).
To learn more about other features we’ve recently added to AXIOM Cyber, check out this blog!
If you’re not already using AXIOM Cyber and would like to try it for yourself, request a trial today.
Mac Acquisition
For years, when investigators have been tasked with examining Mac’s in corporate environments options have been limited in terms of the best way to query and acquire files from the endpoint under investigation, especially in a covert manner. With the release of AXIOM Cyber 4.0, examiners can now select during the agent creation process whether they want to deploy to a Windows or Mac endpoint.
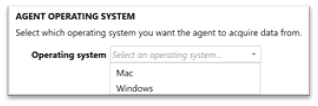
The AXIOM Cyber agent is built on .NET Core which means a bunch of the .NET dependencies are packaged with it as part of the agent creation process. While discussing the agent creation process, we’ve had customers ask if they can whitelist our agent for use in their environment, and while you can do this, it can’t be whitelisted based of hash value due to each agent created is built specific based on the parameters entered during the build process.
Unlike our Windows remote acquisition capabilities where users can select both logical files or the physical disk for acquisition, our macOS agent allows for only logical file collection. AXIOM Cyber leverages operating-system calls (vs bytes from a mounted volume) for the acquisition. While it’s understandable that examiners may need a physical image of corporate endpoints, collecting logical files over the network allows AXIOM to forgo imaging limitations faced when encountering Apple hardware that has T2 chips (Devices from late 2017 on). More information the hardware based encryption provided by T2 chips can be found here. Another hurdle that is avoided with collecting logical files versus traditional physical imaging is System Integrity Protection (SIP). SIP has been around for a little while now having been released in OS X 10.11 (El Capitan), which initially protected:
- /System
- /usr
- /bin
- /sbin
- /var
- Apps that were pre-installed with OS X
SIP only allowed modification of the protected locations by processes signed by Apple. Learn more about System Integrity Protection here. SIP also prevents access to the disk from a physical layer for imaging, so unlike in the past where we could image the Mac while it was on and logged into, that isn’t the case anymore, without SIP being disabled.
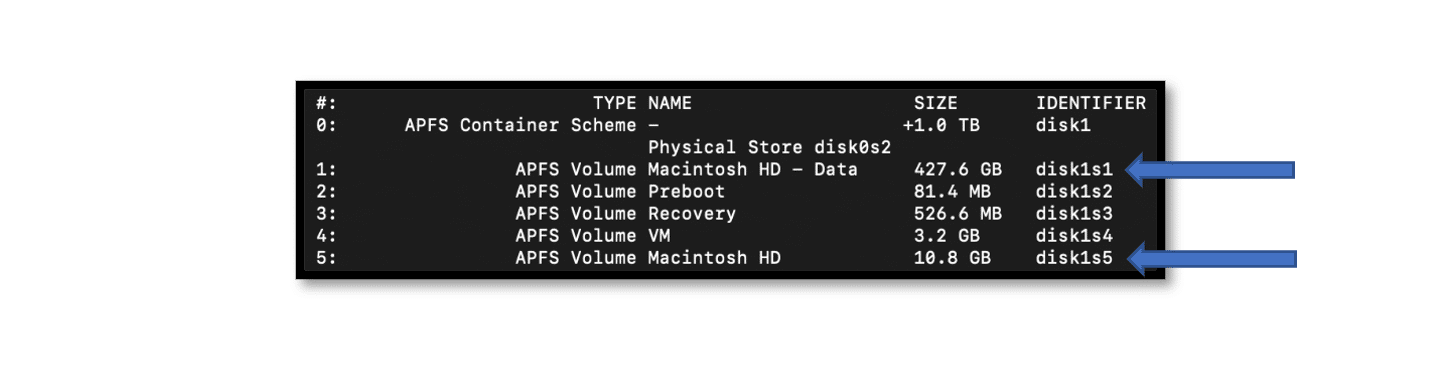
With the recent release of macOS Catalina (10.15) Apple upgraded SIP by instead of protecting specific locations on the same volume, it’s now created a second system volume which is completely read-only. Machines using the standard naming convention will have both Macintosh HD and Macintosh HD – Data. Macintosh HD will contain only the operating system files, so examiners looking for user profile data will typically be interested in the “Macintosh HD – Data” volume. It’s important to note that even though there is a new “-Data” volume, end users will not notice a change on their end. Read more about the changes made during the 10.15 upgrade here!
Forensic Nugget: If you run across a “Relocated Items” folder during an exam and have found a random assortment of files within, this folder is a result of the Catalina upgrade, where Apple migrated any user files that were previously stored in the startup volume, so users would still have access to their data once Macintosh HD became read-only. The Relocated Items folder is placed (Users/Shared/Relocated Items) with a shortcut also being added to the Desktop.
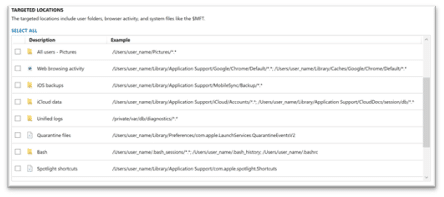
Similarly to what users find when they collect from Windows endpoints, we’ve also added the ability to quickly acquire from pre-packaged targeted locations, removing the need to dig through the file system to find data that is needed routinely in your investigations. This could range from browser history to quarantine files, iOS backups, iCloud data, or the unified log.
Deployment
Once the Mac agent is created in AXIOM Cyber, it’s time for deployment. In order for our agent to deploy we require Remote Login enabled. Remote Login can be found by navigating to:
If an examiner is using a root user (different from admin user with sudo), they will need to enable SSH for root, but this isn’t recommended or feasible in most corporate environments. When Remote Login is activated in settings as discussed above, SSH will be enabled.
AXIOM Cyber’s macOS remote acquisition deployment will attempt to run the agent with sudo if the supplied user credentials have permissions based on the sudoers file. If the user credentials have sudo permissions enabled AXIOM will display the user as root.
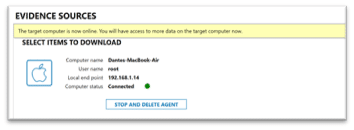
Based on the permissions of the user, Cyber may be limited to what files can be acquired. For example, if a user doesn’t have sudo access, .FSeventsd and .Spotlight-V110 wouldn’t be accessible due to macOS by default only has read/write on those system files with no permissions set for any other users, which means Cyber can’t acquire with an admin account, but can with sudo. Unfortunately, there are still a few files still inaccessible for acquisition even with sudo privileges due to even more restrictive permissions. One example of this would be the Lockdown folder (on 10.15.5) which contains pairing certificates to iOS devices.
What’s Next for AXIOM Cyber
Here at Magnet Forensics, we utilize an iterative and incremental development cycle for our products, and with that comes discussions about the future capabilities we’d like to support. With that, we felt it was important to get Mac remote acquisition into the hands of our customers as soon as possible while we continue development of acquiring and processing mac volatile memory / open processes. Our engineering team is also hard at work integrating alternative output formats for data acquired from remote endpoints, customers will soon have the option of either .zip or AFF4-L as an output format. Lastly, examiners will soon be able to create and save custom targeted locations for data they routinely need to collect versus having to manually select it from each endpoint for every investigation. If there are other artifacts you’d like see supported, please don’t hesitate to reach out, we’d love to hear from you!
Want to learn more? Head over to the Magnet AXIOM Cyber page for more information and request a free trial today!
As always if you have any questions, comments, or product features don’t hesitate to reach out to me at trey.amick@magnetforensics.com