Insider Threats! Using Magnet AXIOM to Prevent and Investigate Intellectual Property Theft

In July 2015, the FBI, in collaboration with the National Counterintelligence and Security Center, launched a campaign to educate businesses and industry leaders about protecting trade secrets and intellectual property. The campaign, which continues to this day, focuses on external threats from foreign-threat actors engaged in corporate espionage, but it also highlights the need to develop insider-threat programs.
Studies show that half of departing employees leave with confidential company information — either deliberately or unintentionally. According to the 2016 Verizon Data Breach Investigations Report, and the 2015 Clearswift Insider Threat Report, several factors motivate employees who deliberately keep company IP, but financial gain is the most common.
Typical IP includes:
- Customer information
- Business plans
- Operational information
- Staff information
- Trade secrets
- Proprietary software
Most organizations now store this type of IP electronically, and employees access it with company or personal digital devices. There are many methods to remove IP from a company, by the most common methods are:
- Personal webmail accounts, such as Gmail or Yahoo
- Portable storage media; USB flash drives are the most common
- Instant messaging programs (including social media programs such as Facebook and LinkedIn)
- Cloud storage such as Dropbox or iCloud
- Accessing corporate systems via remote sessions
You can significantly reduce the risk of data exfiltration or leakage by using digital forensic practices during corporate investigations and exit interviews. These practices include techniques and tools designed to capture, analyze and evaluate digital data as evidence, plus identify if something happened, what happened, when it happened, who caused it to happen or was involved, and evidence to prove it.
Organizations are now seeing the value of embedding these practices into their daily workflows. They’re using them proactively to prevent IP theft rather than potentially be involved in litigation after the fact. In-house forensic staff or external companies can assist with HR, security and privacy needs prior to — or even during — exit interviews to quickly analyze data before staff members leave for good.
How to Use Digital Forensic Practices
Here are practices that you can incorporate into your everyday work routines.
- Data Preservation
To ensure that evidence isn’t permanently deleted, companies can periodically image the systems and devices of employees who have access to company IP. This safeguards any evidence, which might be required at a later date.
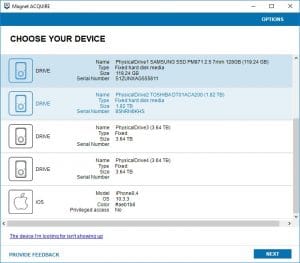
A great method you can use to image a device (computers and mobile) for data preservation is by using Magnet ACQUIRE. This one product allows you to image a variety of mobile devices, hard drives, and removable media. And the best part? It’s free!
- Real-Time Review
Exit interviews help you learn why employees are leaving and find ways the company can improve. However, you can also use them to help determine if departing employees might have taken company IP with them. HR staff can ask questions to learn more about where employees kept company data and if they took it home — and, if so, on what devices and when. While the interview is being conducted, and if warranted, digital forensic practitioners can discreetly review the employees’ device(s) to look for any indicators of IP theft. (Check with your legal counsel to determine limits in your jurisdiction.)
During a real-time review, there is often not enough time to take a forensic image of a device and investigators need to be able to access information quickly about an employee’s activities. One method to do this is by running Magnet AXIOM on a write blocked drive.
Once AXIOM is run, an investigator is presented with the option to choose a computer, or a mobile device.
Using AXIOM for a real-time interview, an investigator should focus on either the drive of the computer, certain Files or Folders, or they can look back into a user’s history by analysing any Volume Shadow Copies.
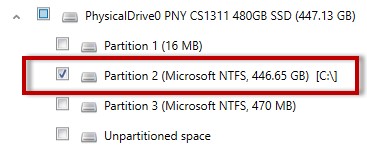
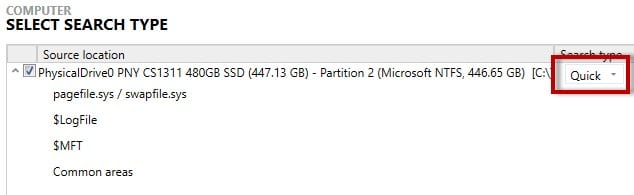
If selecting the drive of a computer, an investigator can focus any analysis on only the partition that contains user data, and then conduct a “Quick” search to look through common areas of the computer that contains user content.
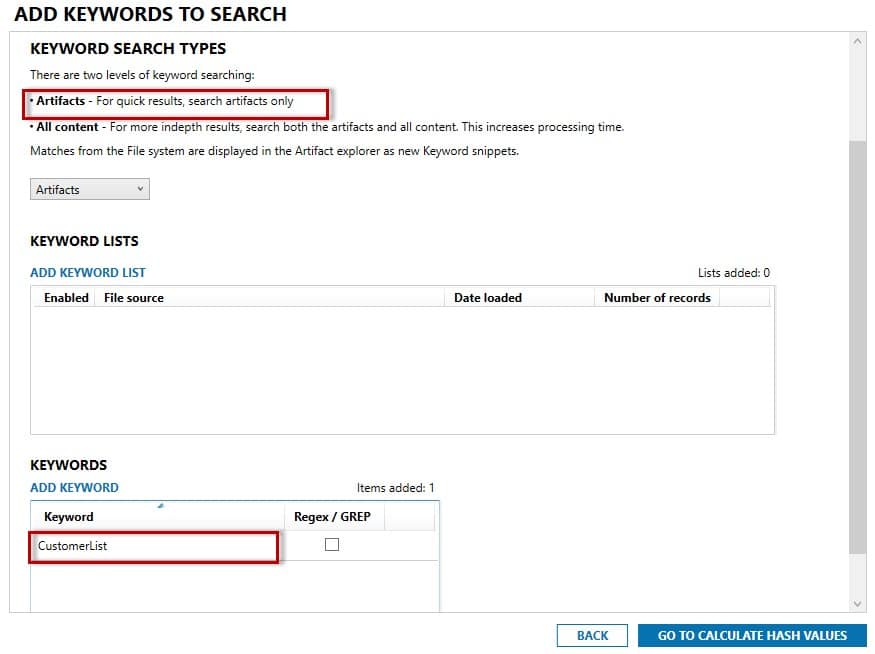
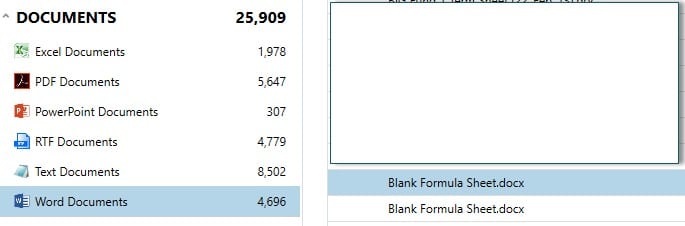
If there are certain documents that are within the scope of an investigation and that the user should/should not have, or should/should not have accessed, you can add any filenames of those documents, or other keywords contained in them to a keyword list prior to analysis.
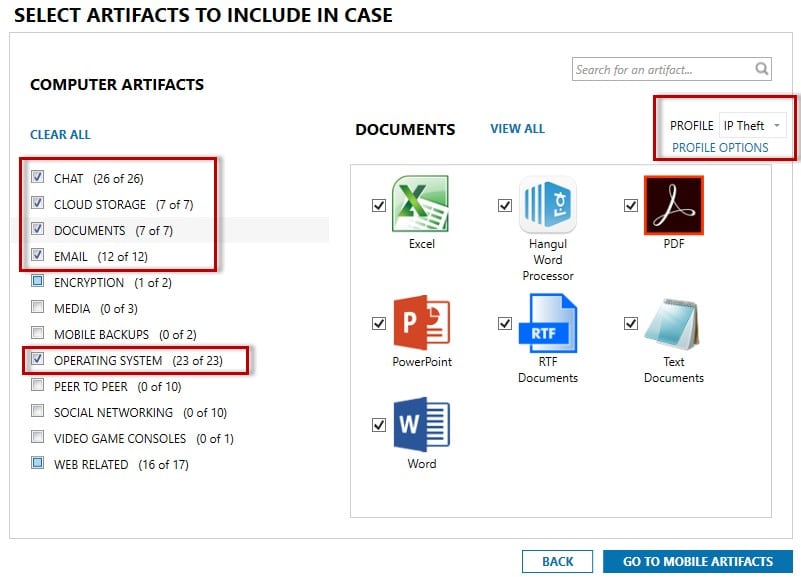
You can then focus your searching only for relevant documents or other artifacts. You can set a Profile for use in future cases. As mentioned earlier, there are many methods to remove IP from a company, such as Webmail, USB usage, Instant Messaging and use of cloud storage.
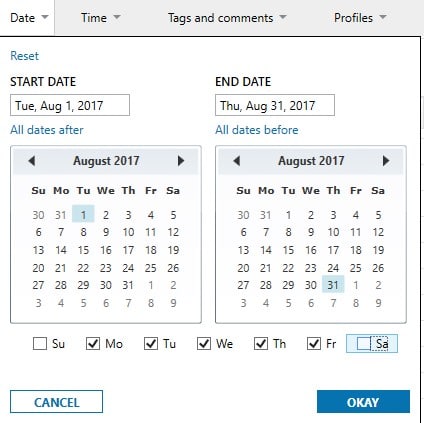
Often the theft of IP occurs a month or two prior to an employee leaving a company, and you can easily filter any evidence based on certain timeframes (even choosing not to include weekends). In the case below, the employee in question resigned on August 31, 2017.
Once the evidence is processed and any filters are applied to the data, an investigator can quickly view the evidence and relay any particulars to the interviewer conducting the exit interview.
- In-depth analysis
If an organization discovers that an employee has left with company data, digital forensics can be used to determine when they took it, how they stole it, who they might have shared it with, and other important elements. (Ed Note: You can now also use Connections in AXIOM to visualize relationships between artifacts and/or files – see where they came from, their attributes and where they went.)
Normally any in-depth analysis is conducted on an “image” of a device and the steps shown in the Data Preservation section above can be used to preserve any evidence. The difference then being, choosing these images within AXIOM for processing and analysis.
Similar to the real-time review, an investigator can customize the areas and which artifacts on a computer or mobile device to be searched and analyzed.
IP Theft Investigation
- Initial Searches
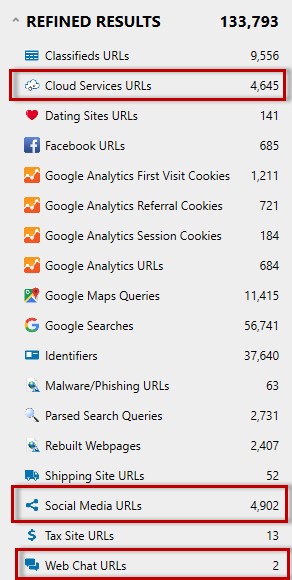
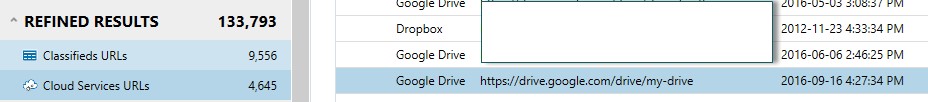
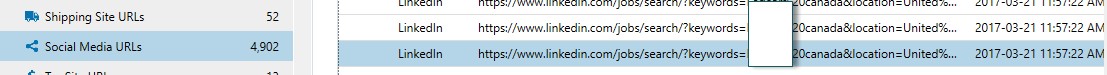
A great place to start an analysis during an IP theft case is within the AXIOM Refined Results section. This area categorizes commonly investigated URLs for quick analysis, contains multiple sources/browsers, and recovers search queries from common search engines. This area allows an investigator to quickly determine various sources of information that may need further examination (such as the use of cloud storage locations, or social media accounts.)
Shows the usage of Google Drive and Dropbox on the system.
Shows the employee searching for jobs at another company and location.
A second valuable location is any browser activity. Artifacts are stored in different locations and in different formats; however, AXIOM will search all browsers and related artifacts in one search. The browser history can provide valuable intel as to other accounts an employee might have been accessing.
- Communications
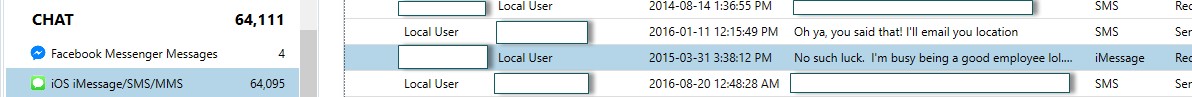
If you suspect the employee in question was communicating with others (in relation to the theft of IP), there are various sources of artifacts within AXIOM that are of value. The first is obviously any mobile device chat files.
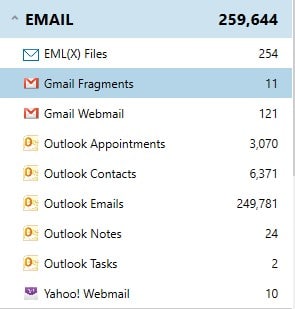
Email is obviously another good source for communications, but certain webmail emails are often not easily found on a system.
Gmail emails for example are often found in browser cache, pagefile.sys, hiberfil.sys, memory and unallocated space on a system. The example below was located with the hiberfil.sys.
- Transfer of IP
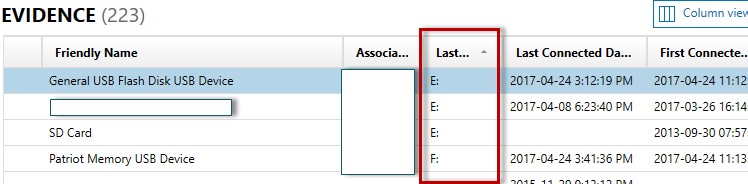
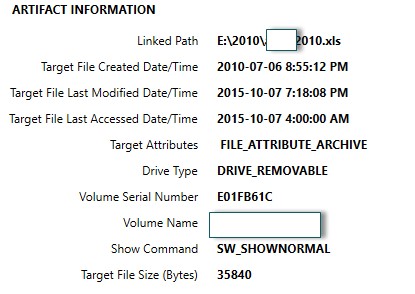
As mentioned, there are often common methods that are used to steal company IP. USB usage is the most common and there are many artifacts that assist in determining any movement of data.
A great place to look for USB usage (and potentially the transfer of any IP data) is LNK Files. LNK files show the original path of a file, and also MAC times for the original document.
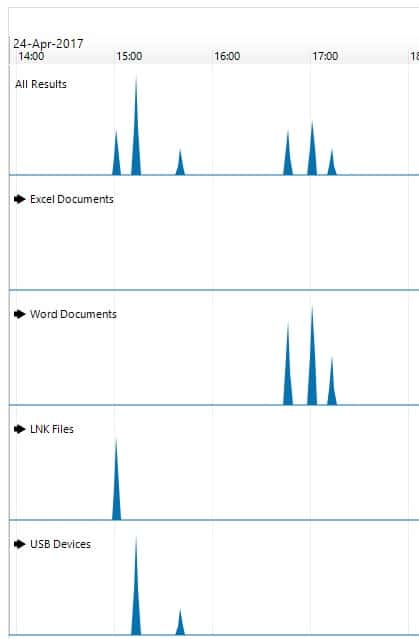
- Timelines
An incredibly helpful feature of AXIOM is the ability to review various artifacts within a timeline view. This gives an investigator a quick view into areas of relevance that may need a deeper dive.
As you are developing insider threat best practices and technology implementations, be sure you look for tools that will help your teams quickly and easily spot trends and connections in the data. It’s also important to find tools that can be understood by others and have solid reporting and collaboration capabilities.
Questions about this blog? Email Ryan at: RyanDuquette@Hexigent.com. Questions about Magnet Forensics products? Email us at sales@magnetforensics.com.