
How to Remotely Acquire from Mac Endpoints Using AXIOM Cyber’s Signed Agent and Jamf Pro
The use of Mac computers for business applications continues to grow steadily. In US-based enterprise companies (1,000+ employees), IDC reported the usage of macOS devices is around 23%, up 6% from 2 years prior. But when Apple made a recent update to their security controls, it prevented data collection from a Mac endpoint without triggering a Transparency Consent and Control (TCC) prompt on the endpoint — which limits acquisition abilities for investigations requiring a more subtle approach.
To ensure you can easily and consistently collect from remote Mac endpoints, we have updated AXIOM Cyber’s Mac agent and had the new agent signed by Apple. Because the agent has been signed, the endpoint automatically identifies the author and application, mitigating Apple’s Transparency, Consent, and Control (TCC) warnings.
To facilitate deploying the newly signed agent to devices running macOS, we have also partnered with Jamf. In speaking with our customers that frequently investigate Mac endpoints, Jamf emerged as the primary deployment tool for Mac and the industry standard in managing Apple endpoints.
In this blog post, we’ll show you how to deploy an AXIOM Cyber Mac signed agent using Jamf Pro in three steps.
Step 1: Create Agent
A standard workflow to follow to utilize Jamf Pro for deploying a remote acquisition agent created with AXIOM Cyber includes creating the agent, uploading it to the Jamf Pro dashboard or an accessible cloud storage location, and then pushing it to your target endpoints.
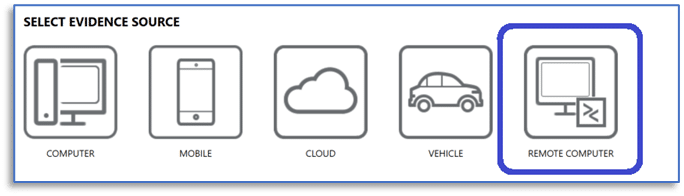
As with other remote acquisition agents, start by selecting the REMOTE COMPUTER workflow from the SELECT EVIDENCE SOURCE screen in AXIOM Process.
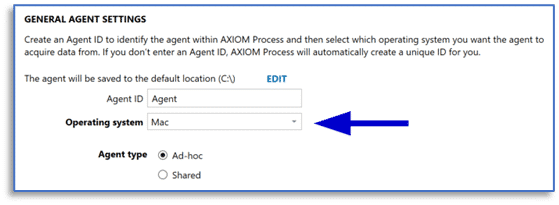
From the MANAGE AGENTS AND ENDPOINTS screen, choose the option to CREATE NEW AGENT and then walk through the agent configuration options, providing the desired agent name and choosing Mac from the Operating system drop-down menu.
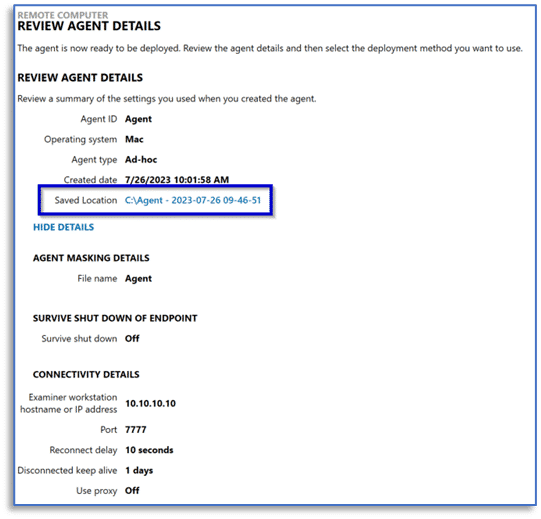
One thing to note, AXIOM Cyber creates remote acquisition agents for macOS as signed applications. This prevents using the typical agent masking options that are sometimes incorporated to prevent the endpoint user from recognizing that a remote acquisition agent is running on their device. Ensure the appropriate connectivity details are configured so that once deployed, the remote acquisition agent can communicate with your installation of AXIOM Cyber. Finally, choose the CREATE AGENT button in the lower right corner of the screen.
From the REVIEW AGENT DETAILS screen, make note of the saved location for the signed macOS agent just created for upload to your Jamf dashboard.
Step 2: Deploy the Remote Acquisition Agent
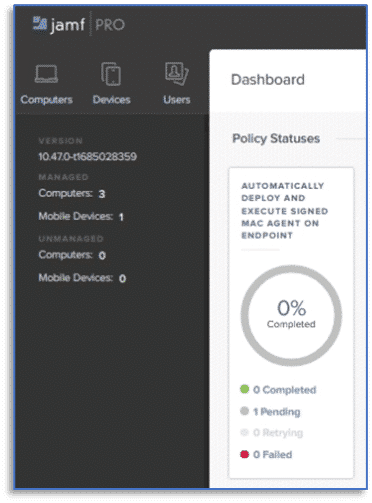
The next step is to log in to your Jamf Pro dashboard and create a policy to facilitate the deployment of the remote acquisition agent. In this example, a policy to automatically deploy and execute the signed macOS agent on endpoints has been created.
Selecting that policy will allow Jamf Pro administrators a variety of configuration options. By selecting the Scripts tab, we can specify the appropriate URL to download the remote acquisition agent, a URL for the agent configuration file, and a folder location to store these files on the target endpoint.
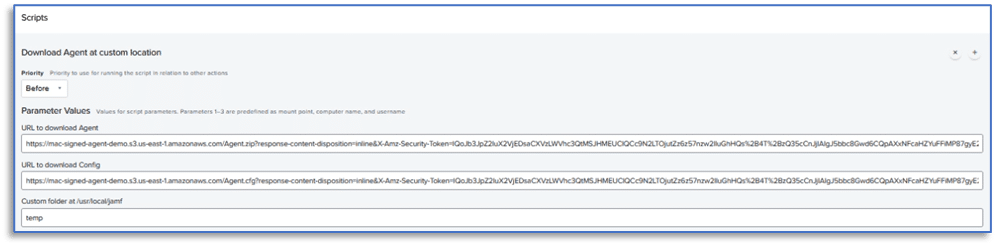
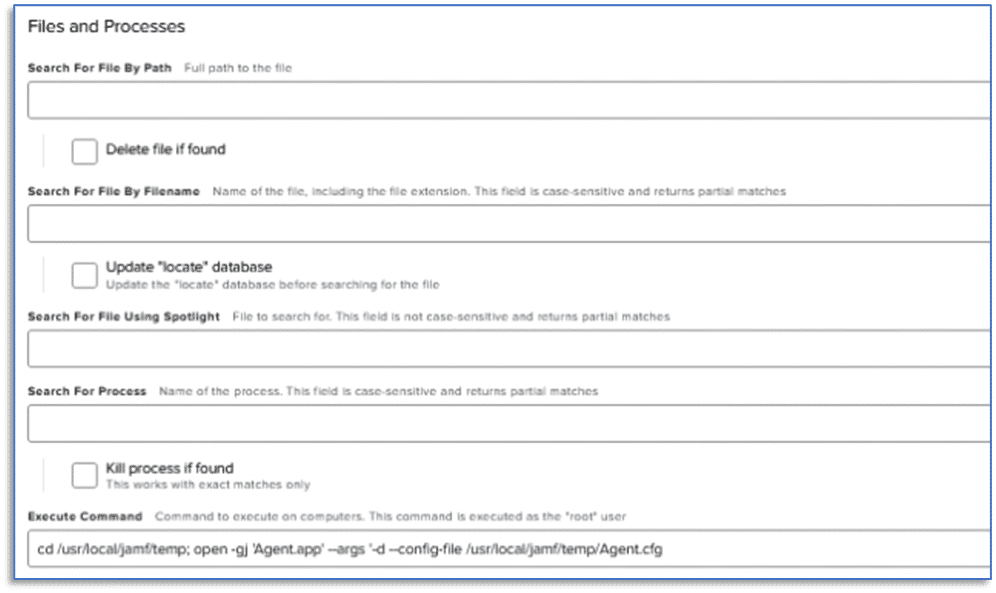
The Files and Processes tab within the Jamf Pro dashboard will allow you to review the command executed on the remote computer. In this example, the Agent.app (signed application created in AXIOM Cyber) will run from the location specified in the Scripts tab. The accompanying command arguments will use the configuration file Agent.cfg and output information regarding the remote acquisition to the AgentLog.txt file specified in the command.
Once you are satisfied with the configuration options, you can return to the Jamf Pro dashboard. According to the frequency specified in your Jamf Pro deployment, the signed macOS remote acquisition agent will be deployed to the endpoint and run at the next endpoint check-in.
cd /usr/local/jamf/temp; open -gj 'Agent.app' --args '--config-file /usr/local/jamf/temp/Agent.cfg'Once the Jamf Pro dashboard indicates the policy as complete, the agent has been downloaded to the target endpoint and is running.

Step 3: Connecting to the Remote Acquisition Agent
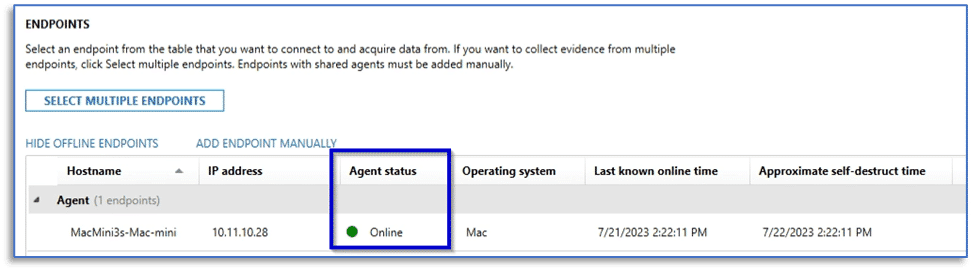
Once the action is marked complete in Jamf Pro, return to AXIOM Process, and the ENDPOINTS window of the MANAGE AGENTS AND ENDPOINTS screen will show the signed macOS remote acquisition agent as online – once it has connected to your installation of AXIOM Cyber.
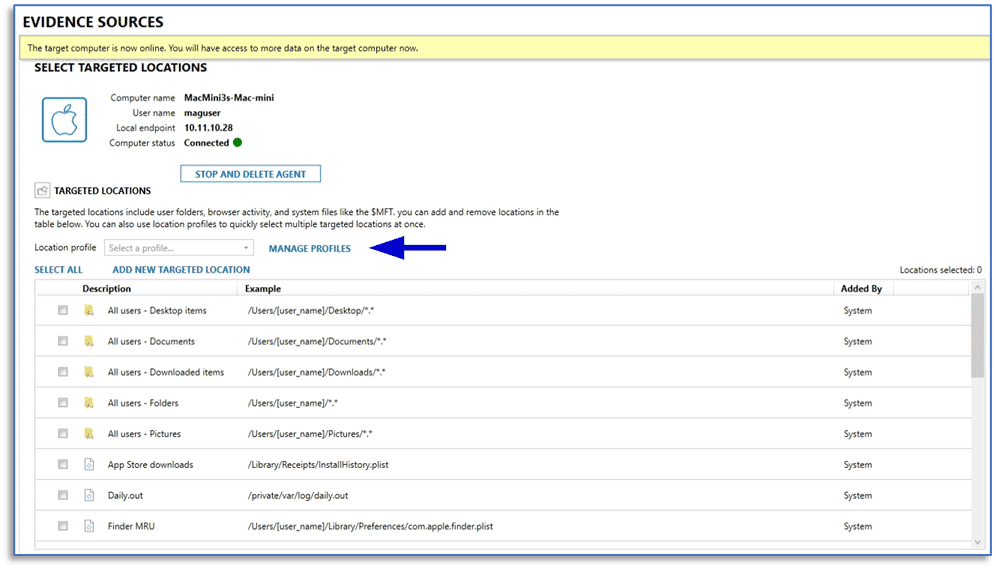
Examiners can then select the CONNECT TO ENDPOINT link and choose the items of interest to download from the remote endpoint. This includes the typical macOS remote acquisition artifacts, options for using targeted locations (and target location profiles), and the files and drives option.
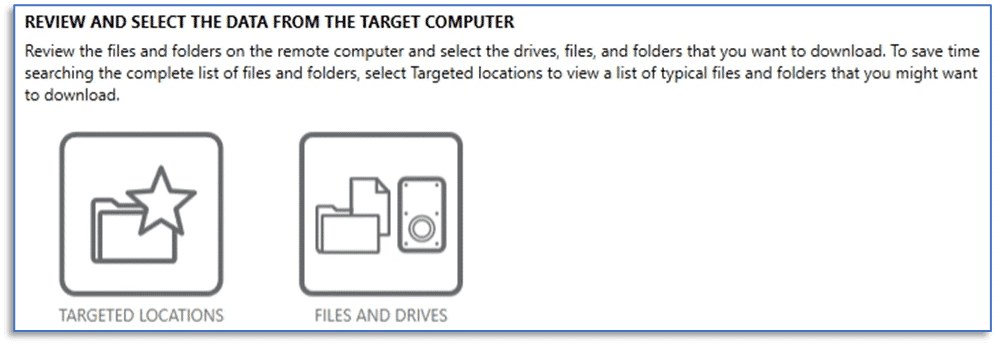
Additionally, examiners can leverage targeted location profiles that have been created in their installation of AXIOM Cyber.
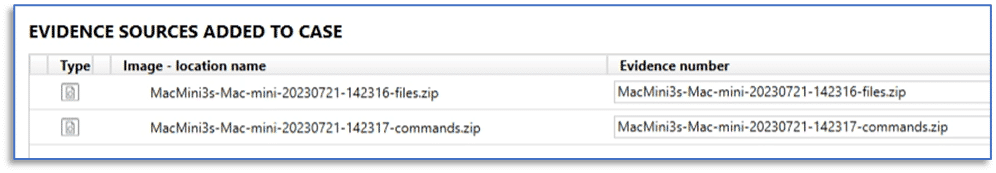
Once the chosen items have been downloaded, they will be hashed and then added to the case for processing.
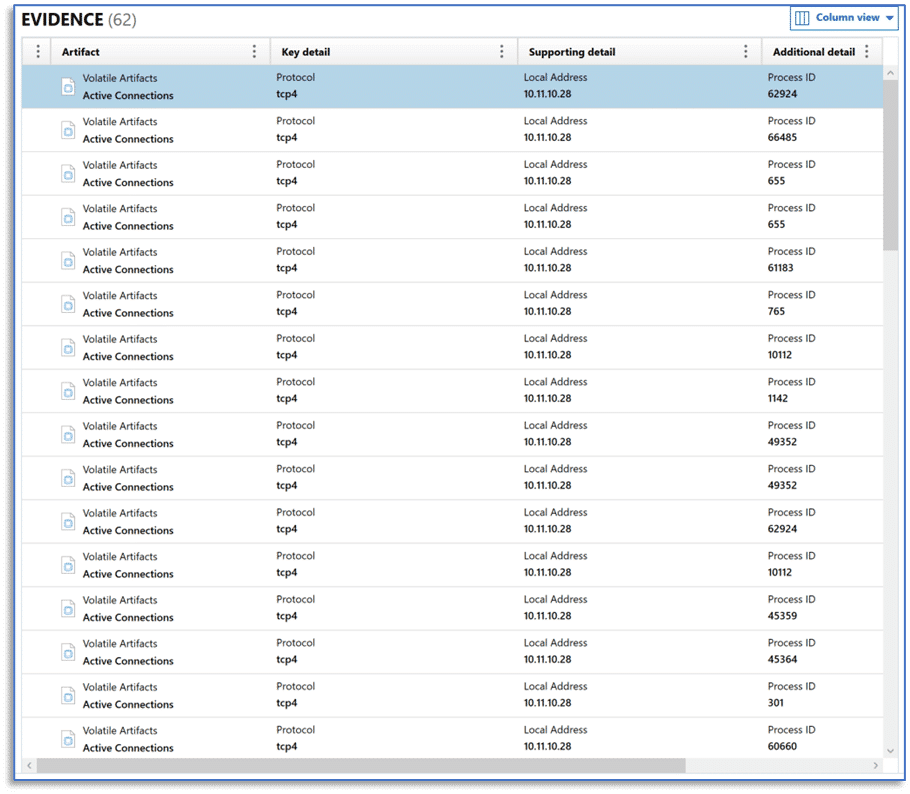
After case processing is complete, you can review the artifacts in AXIOM Examine just as with any other data source. For this example, the remote collection option to obtain the volatile artifacts for active connections and active users was enabled, with a sample of the active connections results shown in the Artifact Explorer of AXIOM Examine here:
This integration will allow customers to seamlessly deploy the new signed Mac agent from Magnet AXIOM Cyber—Magnet Forensics’ robust digital forensics and incident response solution for organizations—onto their macOS endpoints using Jamf Pro Mobile Device Management. If you are an existing AXIOM Cyber user, this functionality is available starting with version 7.4, which you can download from the Customer Portal. If you haven’t tried AXIOM Cyber, request a free trial here to check it out yourself.