How To Get the Most Out of Your Magnet GRAYKEY Extractions
Magnet GRAYKEY extractions are an amazing tool for digital investigators and examiners, since getting a full file system image is crucial.
For years, most forensic examinations of iOS devices were limited to data only available in an iTunes backup and only if you had the user’s passcode—with Android acquisitions not being much easier.
However, in recent years examiners working in mobile investigations have had additional tools in their DFIR tool bag. GRAYKEY has given organizations deeper access to mobile devices, allowing for Before First Unlock (BFU), After First Unlock (AFU), and Full File System acquisitions.
With GRAYKEY extractions, examiners now have tremendous amounts of data that can be vital for their investigations. But that’s only when that extraction is coupled with powerful processing and analysis of key artifacts. With Magnet AXIOM and Magnet AUTOMATE, examiners can parse, analyze, and report on critical evidence to help bring justice to their victims.
Let’s look into how you can get the most out of your GRAYKEY extractions.
How Data Can be Outputted in GRAYKEY Extractions
Data acquired via GRAYKEY extractions may be outputted into a variety of containers (Full Files, mem, and / or a plist).
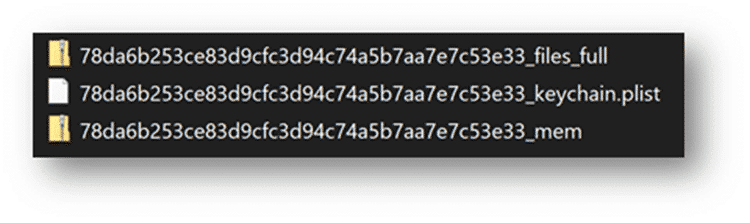
For investigators, the ideal GRAYKEY image when examining mobile devices is the files_full.zip. This has the entire file system present and provides the maximum amount of information usable in the course of an examination. In the references below we’ll be utilizing iOS images, however you can follow a similar path to load GRAYKEY-produced Android images.
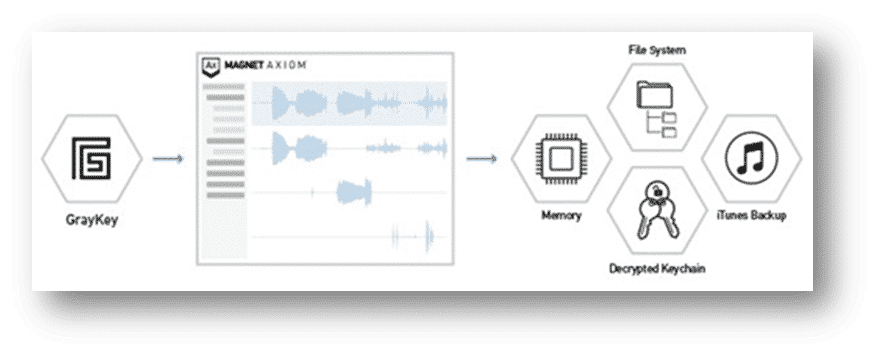
Depending on the type of extraction (BFU, AFU), a mem.zip may also be generated for the device’s memory. This is a process memory dump of the iOS device. Prior to GRAYKEY, examiners hadn’t acquired process memory of iOS devices for routine analysis. The iOS process memory contains valuable information and should most certainly be loaded into AXIOM as well.
A keychain.plist will most likely be generated with GRAYKEY. Most examiners are familiar with the iOS keychain as it contains the user accounts, passwords, and keys for many of the apps that the user has saved or used which can also be valuable for investigators wanting to authenticate to cloud sources or otherwise. The keychain that GRAYKEY creates is slightly different than the one you would get in an iTunes backup or found natively on a jailbroken device. The keychain found in the file system is actually an SQLite database and hasn’t always been available due to limitations in acquisitions prior to this. The keychain in an iTunes backup is also a .plist but is formatted differently, so we’ve added specific support for the GRAYKEY keychain.plist in AXIOM and AUTOMATE.
GRAYKEY will also produce a file named passwords.txt and a PDF report of the device extraction. While the passwords.txt list is great for examiners to look through, make sure to load the keychain.plist into AXIOM for parsing, not the passwords.txt file.
Loading GRAYKEY Images Into AXIOM
There are several ways to load your full file system extraction into Magnet AXIOM. Depending on the method of acquisition, the process for loading the extraction in Magnet AXIOM may vary.
Manual Image Loading
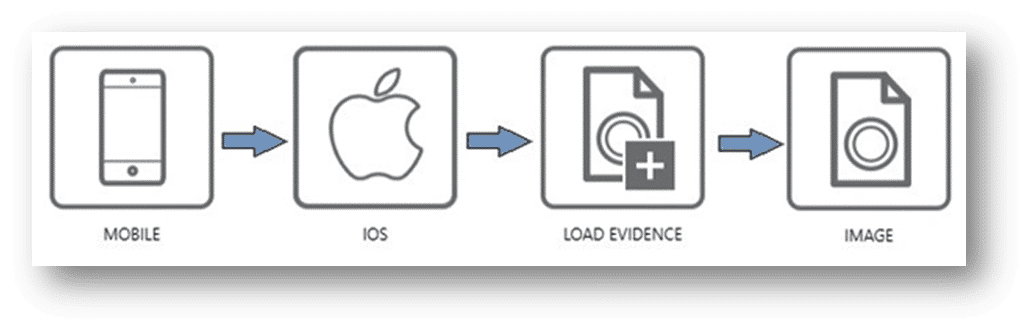
You can follow the same path as most other iOS images by choosing Mobile -> iOS -> Load Evidence -> Image and then choosing the zip files. For GRAYKEY extractions, select the files.zip first, then the mem.zip in the same manner.
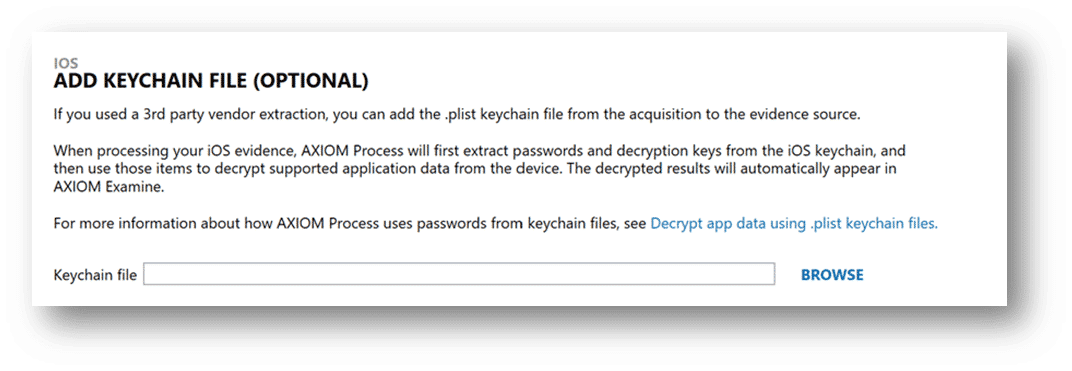
Another option is to load the keychain.plist first to see what credentials it may hold.
When dealing with iOS devices that you have the keychain.plist for, it may be beneficial to process just the keychain and to review the data of that sole piece of evidence before navigating to the Case Dashboard of AXIOM Examine and hitting “Add Evidence”.
Why you ask? Great question!
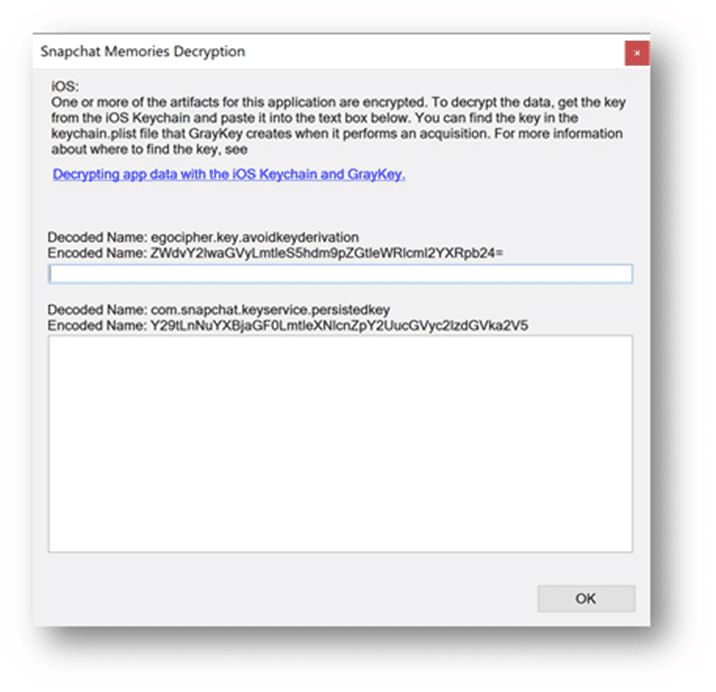
By reviewing the keychain.plist, examiners will have a good idea of the apps that may be found on the suspect device. Better yet, when loading the files.zip into AXIOM for processing, potential passwords can be supplied, along with key values for encrypted apps like SnapChat, WickrMe, or iOS Notes, so during processing, AXIOM can decrypt these databases for the examiner to analyze during the course of their investigation, without the need of having to reprocess the evidence. We’ve added information within the artifact selection category for apps that we can decrypt during processing for examiners to reference when copying information out of the keychain into AXIOM, as seen below.
Loading Via Direct AXIOM Connection
For agencies with an online GRAYKEY there is an additional option when it comes to loading your acquisitions into AXIOM.
The integration between GRAYKEY and AXIOM allows examiners to connect AXIOM directly to their GRAYKEY via a network connection. This direct-connect option has several benefits over the traditional procedure of downloading the images via a browser from your GRAYKEY before starting a case with your analysis software.
The first benefit of using the direct connect option is speed. Using direct integration reduces the steps needed to start your investigation overall, and when it comes to the volume of iOS devices you’re acquiring, this time savings can really add up.
Secondly, AXIOM will prompt you on where to save the GRAYKEY image too as its acquired and processed for examination. As a part of this process, we will also automatically hash the files we are acquiring, so that you can quickly confirm from the GRAYKEY GUI your hash values match. On numerous occasions we’ve heard investigators say that when they loaded their GRAYKEY image into their analysis tool, things seemed “off”, or the image couldn’t be loaded. This is in part to potentially the browser capping the size of the download, or a packet dropping during the download of the image file.
Loading Evidence from GRAYKEY into AXIOM
To load evidence via the direct connect method, choose Mobile -> iOS -> Connect to GRAYKEY. Once connected, you can browse the available data that is saved on the GRAYKEY, selecting the different evidence files you wish to acquire and process with AXIOM.
Check out the video below on utilizing the Connect to GRAYKEY feature in AXIOM:
Initiate AXIOM Processing from GRAYKEY
In addition to loading GRAYKEY images from AXIOM, GRAYKEY users can also choose to automatically download a mobile device image into AXIOM Process once it has been extracted directly from the GRAYKEY user interface. AXIOM automatically validates that the files were correctly loaded using the images hashes and will then process the case. Users will be able to monitor detailed progress status of the AXIOM image processing through a GRAYKEY web dashboard.
Check out our blog for more details on how to enable AXIOM image processing from GRAYKEY.
Creating Automated GRAYKEY Workflows with AUTOMATE
For customers with Magnet AUTOMATE deployed in their lab, automated mobile end-to-end workflows utilizing GRAYKEY images can quickly be created and kicked off. AUTOMATE orchestrates processing and output generation across all your mobile cases, eliminating many of the manual interactions required helping to dramatically reduce your time-to-evidence.
AUTOMATE’s intuitive Workflow Builder makes it easy to design automated end-to-end mobile workflows leveraging GRAYKEY, from imaging to processing through to reporting. Once you’ve added your GRAYKEY to your list of available imagers, you can use the Workflow Builder’s drag-and-drop interface to create your own custom workflows for iOS and Android devices incorporating AXIOM or any of your other forensics tools and processes. AUTOMATE can automatically kick off each step of the workflow without the need for examiner intervention.
With your workflow created, you can now begin your investigation by creating a new case within AUTOMATE, adding the case details and examiner information. Then choose the appropriate workflow, select your GRAYKEY image, and AUTOMATE will then automatically verify the image before allowing the keychain processing box to be selected along with the corresponding keychain.plist.
Lastly, the examiner will need to define where the case outputs for the GRAYKEY image will reside. Many customers mention they create a folder alongside their GRAYKEY Image to make grouping evidence and outputs together easier later.
Want to know more about how GRAYKEY and Magnet AXIOM can work together? Reach out to us at sales@magnetforensics.com for more information. For more on mobile forensics, check out Chris Vance’s Mobile Unpacked webinar series.