
Free Mac & iOS Resources for the DFIR Community
Members of the forensic community often take it upon themselves to create scripts, custom artifacts, or software to aid in their investigations, then share with others, which I’ve always loved. The talent our community guild has is truly awesome, and I’m thankful to be a part of it. This blog isn’t meant to be an end all, be all of every publicly available Mac resource, but to highlight a variety of projects from around the community.
We’ll talk about it more later in this article, but make sure to also check out our Free Tools. We’ve recently updated several of them, and while they aren’t specifically for Mac or iOS they can be used in those investigations as well.
iLEAPP
Originally unveiled to the public December of 2019, Alexis Brignoni has been hard at work updating iLEAPP, with the latest version, 1.2 just recently being released. iOS Logs, Events, and Properties Parser or iLEAPP, is a combination of different stand-alone scripts centralized into one tool for parsing things like the Mobile Installation Logs, iOS Notifications Content, among many other files. iLEAPP also parses bplists found within the iOS KnowledgeC.db, as well as KnowledgeC fields including:
- Application Usage
- Application Focus
- Application Activity
- Battery Level
- Applications Installed
- Device Locked
- Plugged In
Other artifacts parsed include Powerlog information, Safari History, Call History, and SMS. This tool is a fantastic resource for the community, whether it’s being used in conjunction with commercial DFIR tools for validation, or as a standalone tool for labs that are faced with budget constraints and need iOS parsing capabilities.
Alexis has been insanely busy in the last year and is currently nominated for several Forensic 4:cast Awards including: DFIR Article of the Year, iLEAPP: iOS Logs, Events, and Properties Parser, as well as DFIR Social Media Contributor of the Year, DFIR Groundbreaking Research of the Year for iLEAPP, DFIR Non-commercial Tool of the Year, and finally Digital Forensic Investigator of the Year! Make sure to head over to Forensic4Cast and vote!
Head over to his website to learn more about both iLEAPP and his complimentary Android tool, ALEAPP – Android Logs Events and Protobuf Parser!
iOS 13 Images
Josh Hickman (thebinaryhick.blog) has provided a much needed community resource with the release of his iOS 13 images. Not only was he kind enough to provide us with iOS 13.3.1, he went ahead and created a second image for download with iOS 13.4.1 as well.
These images allow for the community to utilize the same data sets during research / testing, so that we can compare outputs from various tools and scripts. Josh’s iOS 13 images can be found here. If you’re in need of an Android 10 image, Josh has you covered as well. You can find that image here.
Disk Arbitrator
For years examiners have utilized Target Disk Mode (TDM) as an option when acquiring Mac endpoints. Recently with the T2-based Macs, this has become even more popular due to the security enhancements made where by default Macs don’t allow booting from external devices / imagers. When connecting to target endpoints utilizing options like TDM, we need a way to protect from mounting the system read/write to preserve our evidence.
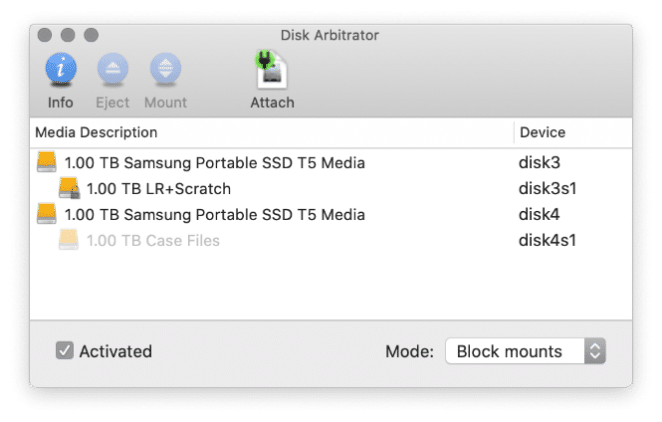
Creator, Aaron Burghardt, states on his github, “Disk Arbitrator is essentially a user interface to the Disk Arbitration framework, which enables a program to participate in the management of block storage devices, including the automatic mounting of file systems. When enabled, Disk Arbitrator will block the mounting of file systems to avoid mounting as read-write and violating the integrity of the evidence.” You can find Disk Arbitrator on Aaron’s Github here.
mac_apt
Brought to you by Yogesh Khatri, mac_apt is a python-based framework for parsing macOS artifacts. I had the pleasure of seeing Yogesh’s presentation during the Magnet Virtual Summit, and seeing mac_aft in action. If you didn’t get a chance to tune in for his initial talk you can find it here, on demand.
With numerous plugins, its cross-platform capabilities, and the ability to work with .E01’s, DMG’s, and .AFF4 images this is quite a powerful platform. We’ll cover how we utilize mac_apt in conjunction with AXIOM and our free tools later in this article, but I really appreciate the SQLite output Yogesh offers with mac_apt. As of the v0.5-beta release, mac_apt also supports macOS 10.15 (Catalina) with the separate System and Data volumes as well. (You can learn more over at Yogesh’s website or follow him on Twitter!
Alongside the mac_apt, Yogesh has also created Deserializer for use with macOS and iOS PLists. Deserializer coverts NSKeyedArchive Plists into normal, unserialized ones that can easily be read. Find more about this resources over on his Github here.
Mushy
If you’ve done a Mac or iOS exam, you know how much Apple loves Plists. Ian Whiffin (Twitter), over at DoubleBlak Digital Forensics has several utilities for the community, but I want to highlight Mushy in this blog. Mushy is a great property list (PList) viewer for Windows!
The latest version of Mushy just landed as of June 7 (v. 1.2.6.0). Users can simply drag and drop the Plist /BPlist into Mushy to review the data. Simple, and easy to use!
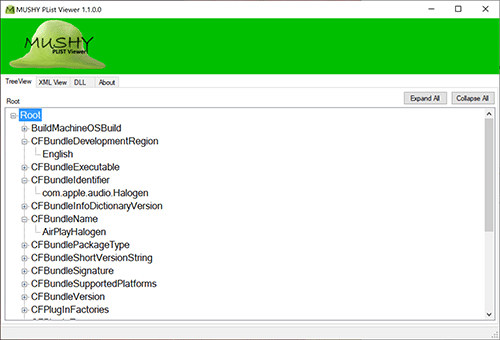
When you head to the website, you’ll first need to register for a free account before you can access the software page. Once complete, you’ll have access to the utilities that are open to the entire community! Ian also has ArtEx-Artifact Examiner which helps visualize the iOS KnowledgeC database, as well as a time stamp conversion tool, and Snoopy, which parses SnapChat’s chatConversationStore.plist. Ian’s blog is packed with tons of useful information for examiners wanting a great break down of Plist decoding — check out this article Ian wrote!
Apollo
Winner of the 2019 DFIR Article of the Year and DFIR Groundbreaking Research of the Year, Sarah Edwards’ article “Knowledge is Power” and APOLLO (Apple Pattern of Life Lazy Output’er) have been a tremendous resource for the community. Providing content to investigations around a user’s pattern of life can be critical and with APOLLO’s multitude of modules, we can break down information ranging from device states to connections and application usage. The amount of data APOLLO provides by correlating data entries across multiple databases with thousands of records is truly awesome! If you haven’t, make sure to check out the APOLLO project over at Sarah’s github.
Sarah also posts a ton of great content on social media and of course on her blog!
Magnet Custom Artifact Generator (MCAG)
Announced last month during Magnet’s Virtual Summit, the free Magnet Custom Artifact Generator (MCAG) makes short work of creating new custom artifacts for use in AXIOM. MCAG accepts CSV/delimited files and SQLite databases for generating new artifacts. Check out Jessica Hyde’s blog here on how to utilize MCAG in conjunction with tools such as Alexis Brignoni’s iLEAPP, or Yogesh Khatri’s Mac Apt.
Now we don’t natively support displaying the unified log from APFS datasets in AXIOM, however many of our artifacts are derived from information we have pulled from the unified log during processing. This is due to the sheer size and number of artifacts the unified log would add to an AXIOM case file if it was fully processed (millions additional artifacts for review).
For investigations that examiners need to go a step further to view the unified log there is an easy way now to load those into AXIOM. First, utilizing Yogesh’s mac_apt, export a SQLite database out containing the unified log. Next head over to our free tools page an download MCAG. Once downloaded, you’ll point MCAG to your SQlite.db that you created from Mac Apt and configure MCAG to create a custom artifact for parsing the database (of the unified log). Lastly, open AXIOM Process, load the SQLite database containing the unified log into AXIOM (Computer>Mac>Files & Folders) and make sure your custom artifact is loaded into AXIOM. Once processed you’ll be able to investigate the log directly in AXIOM.
Archival Tools

While not forensic utilities, employing Macs in your lab means there will be a need to decompress / open archival based formats from a variety of sources. While Macs come standard with the Archive Utility.app, users can run into issues with trying to open specialty files with it. I recommend checking out either The Unarchiver application found here, or Keka found here. Both have great features and work well to open from a variety of sources the standard Archive Utility struggles with. Personally, I utilize Keka, which offers different default compression formats, and can even be set to exclude macOS resource forks (ex: .DS_Store) for use in mixed endpoint environments. Keka also works well with 7zip based archives.
Wrap Up
While there are many additional Mac utilities out there, I hope everyone takes a few minutes to check out the few covered in this blog. Using the different projects in conjunction with your commercial tools makes for a strong combination both with the validation of the data you are working with as well as making evidence collected actionable, faster. If you have other utilities you’d recommend, please feel free to email me at trey.amick@magnetforensics.com