Using F-Response and Magnet AXIOM: Use Case 2 – Preview No Artifacts
When conducting remote enterprise investigations, one of the biggest challenges is pulling large amounts of data over the network. Previously we’ve discussed how to use F-Response Enterprise and Magnet AXIOM (Using F-Response and Magnet AXIOM to Conduct Enterprise Investigations) to acquire and analyze remote machines. We’ve also discussed how to conduct a targeted acquisition (Using F-Response and Magnet AXIOM: Use Case 1 – Targeted Acquisition) to minimize the amount of data that gets pulled over the network while still accomplishing the objectives of the investigation. This blog will discuss another method you can use to limit the time it takes and the data that gets transferred over the network.
For some investigations, you may not want to acquire anything at all, you simply want to preview or analyze the data on a live system with minimal impact to the user or system. F-Response Enterprise and Magnet AXIOM will also facilitate this.
First, you must establish the network connection between your examination machine and the target computer using F-Response (we discuss how this is done in the previous blog). Once the connection is established and the target drive is mounted, it should be visible to your examination machine either via Windows Explorer or more preferably through your forensic tools as a physical disk.
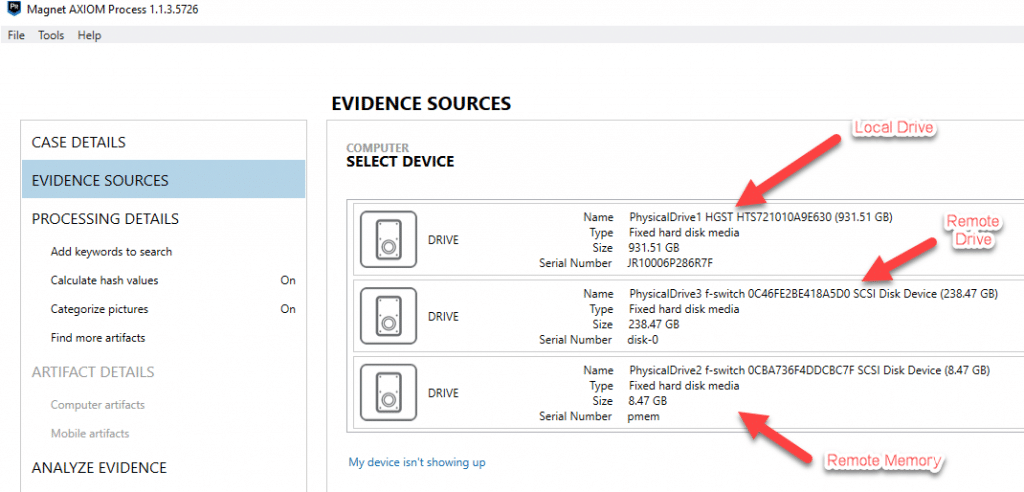
At this point, you can choose to acquire the evidence over the network for processing afterwards, or you could simply process just the file system to get a quick preview of the files available on the system. This can be helpful in determining if the system you are connecting to is the correct target machine which you may want to confirm prior to doing a full analysis on.
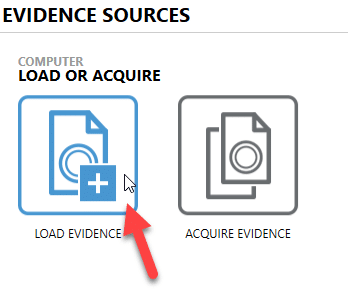
To do this with Magnet AXIOM, open AXIOM Process (AXIOM has two areas within it – AXIOM Process has the acquisition and processing features, while AXIOM Examine has the analysis capabilities), go to “Evidence Sources”, and choose “Computer.” From there, instead of choosing to acquire the disk, you can select “Load Evidence” and point it to the remote target drive. This will allow you to process the remote machine without acquiring an image.
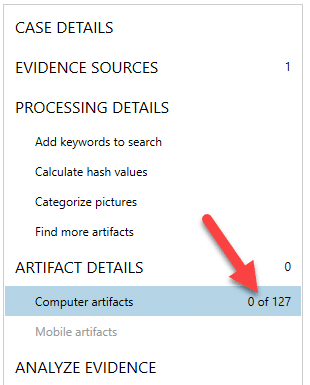
Once loaded, you can choose your processing options including: keywords, hash lists, and artifacts. For a quick preview of just the file system disable these options and choose no artifacts. This will simply build the file system and enumerate the files found on the system.
Once processing is complete, you will be presented with zero artifacts from AXIOM Examine but if you switch from the Artifact Explorer to the File System Explorer, you will get a full preview of the file system of the remote machine.
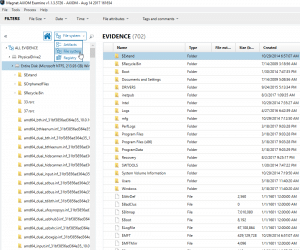
From here you could review the data available to the file system and choose to either go back and acquire the remote computer or disconnect and move on to the next system. Just remember, this is for quick previewing, if you want to take advantage of the artifact analysis capabilities and other processing features AXIOM has to offer, you would need to re-process the drives or acquire and process the drives.
Any questions? Send an email to Jamie at jamie.mcquaid@magnetforensics.com.