
Exploring the significance of jump lists in digital forensic examinations
What is a jump list? The term “jump list” is used quite frequently in digital forensics and discussions regarding artifacts found on computers. A jump list provides users quick access to recently used files, tasks, or applications. The primary purpose of a jump list is to enhance the user experience and productivity by allowing the user to easily navigate to frequently accessed items without having to search through directories or menus. Many users and digital forensic examiners quickly think of Windows when discussing jump lists, but you can also find them on other operating systems, such as MacOS as well.
So, what exactly is a jump list? A jump list is a dynamic menu containing recently accessed files, tasks, or applications. Jump lists were created to allow users quick reference to important or recently used items without having to search for these items on the computer. One of the easiest ways for a user to check their jump list is to right-click any icon in the taskbar. This will bring up the most recently accessed items from that program. In the Windows environment, you can see recently used programs and files by clicking the Start Button (or Icon) and looking at the Recommended items. This can also be expanded out in Windows 11 to show additional file history.
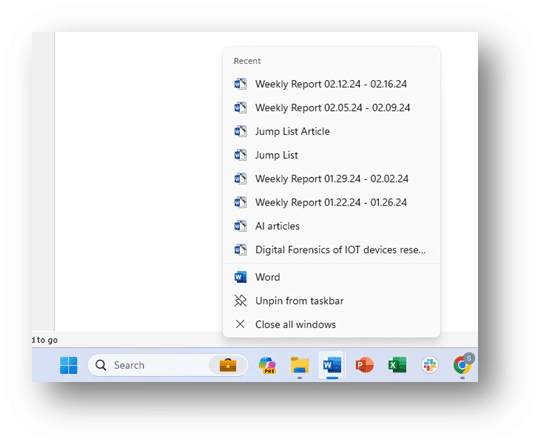
Now that we have a basic understanding of what a jump list is, let’s discuss the components of a jump list and how they relate to the digital forensic investigation of a computer. Jump lists contain many relevant data points related to a digital forensic investigation. These artifacts include file paths, task information, timestamps, application information, user-specific customization, icons, thumbnails used, Jump count, and security identifiers. We will address each of these artifacts.
File Path and Task Information
Jump lists store detailed information about recently accessed files and tasks, including their full paths and associated metadata. This component is crucial for digital forensic examiners as it directly links to the content users interacted with on the system. The inclusion of file paths allows investigators to trace the history of specific documents or applications, aiding in the reconstruction of user activities and potential evidence discovery.
Timestamps
The timestamps associated with jump list entries are fundamental for establishing a chronological timeline of user actions. Digital forensic examiners heavily rely on this temporal information to reconstruct events accurately. Timestamps enable investigators to correlate activities, identify patterns, and ascertain the sequence of actions taken by users, providing a crucial context for the overall forensic analysis. Timestamps in jump lists provide a plethora of data regarding file usage. Some of the most common and useful data for a forensic examination include the created date and time, the last modified date and time, and the last accessed date and time. During the examination, it is also important to note that in their raw format, these dates and times are based on UTC (Universal Time Coordinated), and the offset to the local time needs to be established. Using tools such as Magnet Axiom will automatically assist in translating this offset.
Application Information
Jump lists include details about executed applications, offering insights into the software environment on the system. This information is valuable for digital forensic examiners to understand which programs were actively used or manipulated. It assists in profiling user behavior, identifying authorized and potentially unauthorized applications, and establishing a comprehensive overview of the digital landscape under investigation.
User-Specific Customization
The ability for users to customize their jump lists by pinning specific items or tasks holds significance in forensic examinations. Pinned items may represent files or applications of particular interest to the user, potentially serving as evidence or indicators of specific activities. Examining these customized elements gives examiners a tailored view into the user’s priorities and frequently accessed content.
Icons and Thumbnails
Icons and thumbnails in jump lists contribute to a user-friendly experience, offering visual cues for quickly identifying files or applications. In a forensic context, these visual elements can aid investigators in efficiently categorizing and recognizing items within the jump list. The inclusion of icons and thumbnails enhances the interpretability of jump list data, facilitating a more intuitive understanding of user interactions.
Jump count or frequency
The jump count or frequency information in jump lists indicates how often a particular file or task has been accessed. This component assists forensic examiners in identifying items of interest that the user regularly uses. Patterns of access frequency can reveal user habits, preferences, or potentially malicious behavior, adding valuable context to the investigation.
Security Identifiers (SIDs)
In Windows environments, the inclusion of Security Identifiers (SIDs) in jump lists is crucial for user attribution. SIDs link specific actions to individual user accounts, aiding investigators in determining who performed specific actions on the system. This association enhances the accuracy and accountability of forensic findings, contributing to the overall integrity of the investigative process.
Jump lists emerge as a treasure trove of valuable information. As seen above. the components found in a jump list can significantly enhance the depth and accuracy of a digital forensic investigation and subsequent forensic report. Using jump list analysis can play a pivotal role in reconstructing the timeline of events on a system. Timestamped entries help to develop a timeline of user activities. The ability to profile a user’s activities by examining the files, applications, and tasks provides valuable insight into the user’s behavior.
A prime example is looking at the file path for saved files. Most users have a central place where they store their data. Following a jump list path can lead to additional evidence. Another scenario is where a user saves data to a drive not seen on the computer. This will indicate to the examiner that they need to find the other device or drive to find that evidence.
Investigators can also correlate jump list data with information from event logs, browser history, or file system artifacts. This correlation enhances the investigator’s ability to cross-reference findings, validate timelines, and draw conclusions about actions taken by the user. All of this leads to defining the user attribution. The key is to use as much of this information as possible to identify and place a user at the keyboard when events occur on a system.
A prime example of this is a recent investigation centered on an individual and his “deleted” files. The subject stated that he did not have the files in question, nor had he ever had access to the files. Although the files were not found on the device, the jump list showed that the suspect had opened the file using a computer software program. The investigation also revealed that the file had been saved to an external USB. Further analysis showed that the suspect had checked his personal bank account five minutes before opening the file and then sent an email (to his mother) soon after accessing the file in question. Magnet Axiom does a tremendous job in breaking out jump list items. As seen in this example, an entry for “Jump Lists” can be found in the Artifacts pane under Operating System.
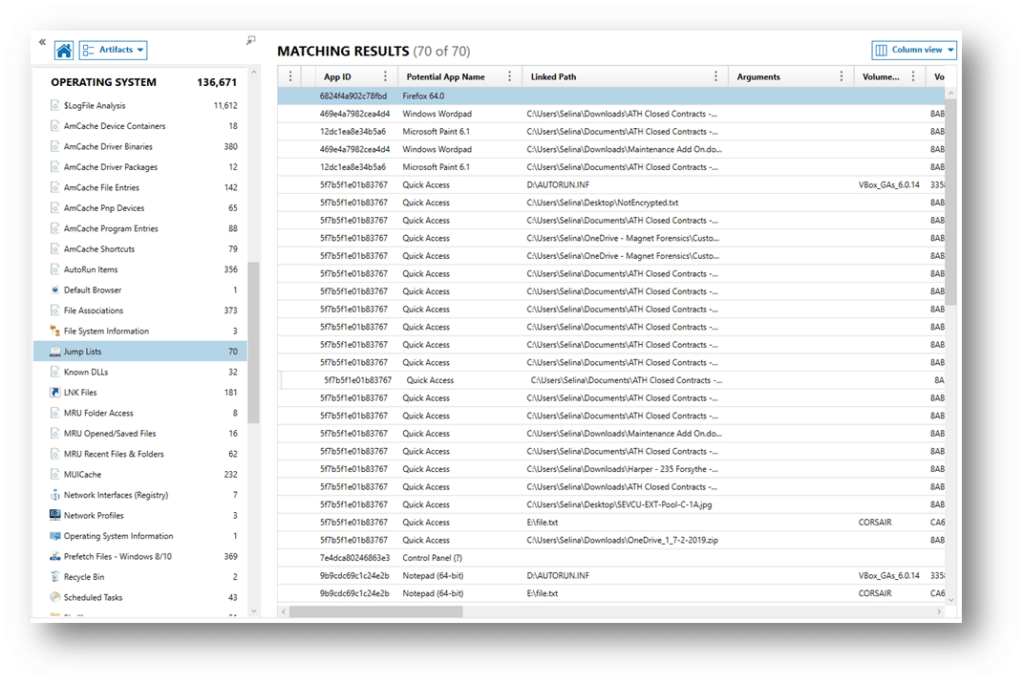
Magnet Axiom will also break out the Most Recently Used (MRU) folder access, MRU Open/Saved Files, and MRU Recent Files & Folders. These can be found right below the Jump List artifact.
Using Magnet’s Axiom, jump lists can be recovered via parsing of the image. Axiom recovers a tremendous amount of relevant artifact information. Some of these artifacts include:
| Attribute | Description |
| App ID | The unique application identifier generated by Windows based on the install location. |
| Potential App Name | A potential application name from a list of common applications and install locations. |
| Linked Path | The path to the target file. |
| Arguments | Any commands being passed to the target file. |
| Volume Name | The name of the volume where the shortcut resides. |
| Volume Serial Number | The Serial Number of the volume. |
| Target File Created Date/Time – UTC (yyyy-mm-dd) | The date and time when the shortcut target file was created. |
| Target File Last Modified Date/Time – UTC (yyyy-mm-dd) | The date and time when the shortcut target file was last modified. |
| Target File Last Accessed Date/Time – UTC (yyyy-mm-dd) | The date and time when the shortcut target file was last accessed. |
| Jump List Type | The type of jump list (Automatic or Custom). |
| Drive Type | The type of drive for this shortcut |
| Target NetBIOS Name | The machine name on the network that the shortcut is on. |
| Target MAC Address | The MAC address of the volume that the shortcut is on. |
| Target File Size (Bytes) | The size of the shortcut file. |
| Last Accessed Date/Time – UTC (yyyy-mm-dd) | The last time that the shortcut entry was accessed. |
| Entry ID | The entry ID. |
| Data | Other data within the shortcut entry. |
| NetBIOS Name | The machine name on the network. |
| Pin Status | Indicates whether the shortcut was pinned in the Dest List. |
| Access Count | The number of times a file is accessed through a Jump List. |
Jump list analysis is a tremendously powerful asset in the toolkit of digital forensic investigators. From reconstructing timelines, profiling user activities, correlating with other artifacts, and establishing user attribution, jump lists enhance the investigative process. Forensic practitioners are encouraged to explore, refine, and integrate jump list analysis methodologies to unlock their valuable insights that they hold within the labyrinth of user interactions on Windows-based computer systems.