
Examining Twitter Warrant Returns with AXIOM
Twitter warrant returns can easily be examined and analyzed using AXIOM. The data provided to investigators containing a user’s activity is ingested into AXIOM then parsed into categories for simple analysis using the Artifacts Explorer.
You can upgrade to AXIOM in-product or over at the Customer Portal.
If you haven’t tried AXIOM yet, request a free trial here.
Getting Started
After obtaining the warrant return data (often in a zip file), examiners can select “Cloud” and then “Load Evidence”, then select “Twitter”, “Warrant Return” and browse to the zip file.

Leave the rest to AXIOM for parsing and categorizing of artifacts that become readily available for review for further analysis.
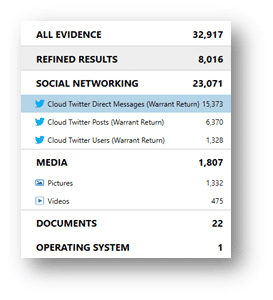
Within the Artifacts Explorer examiners will find Twitter Direct Messages, Twitter Posts (Tweets) and Twitter Users either followed or following the suspect account. As you can see in the graphic below, Pictures and Videos are accounted for in the Media category. Both also have a Preview card in the Details pane, as well as a playable preview for videos.
Examiners can select, “tools” and then “build Media Explorer” for more detailed analysis of pictures and videos. Additionally, after building Picture Comparison, the media items can be compared with pictures within the warrant return or from an external picture using CBIR (Content Based Image Retrieval) technology built into AXIOM. For more information about CBIR, check out this blog.
Twitter warrant return data can be processed in AXIOM along with device data and publicly acquired data or user account data. And, as always, taking advantage of Timeline and Connections within AXIOM can help examiners identify the most important case artifacts.
If you have any questions, please don’t hesitate to reach out directly via kim.bradley@magnetforensics.com.