
Don’t Let a Proxy Server Stop Your Remote Collection
Many enterprise organizations will leverage proxy servers to segment their network and improve their security posture. When performing remote collections of target endpoints, you have to make sure that you’re using a tool that is aware enough to identify when a proxy server is being used, and then still successfully complete that remote collection.
Magnet AXIOM Cyber can do just that! And even better, it only takes one click to enable. No advanced configuration needed, no need to engage with IT or other teams. The end result is a simplified workflow that saves the examiner time and energy.
Here’s How it Works
Endpoint proxy detection within AXIOM Cyber allows organizations to deploy and collect across segmented networks in a simple but effective manner.
As we can see below in Figure 1, during the creation of the agent in AXIOM Cyber users will see a check box under the connectivity details section for the endpoint proxy detection functionality. Please note that proxy detection is off by default and will need to be selected at the time the agent is created. Once selected, the agent will check for the proxy configuration from the Proxy Auto-Configuration (PAC) file on the endpoint.
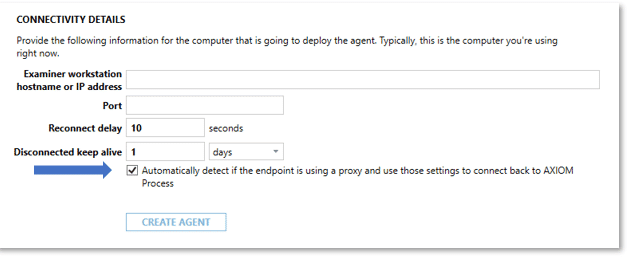
A couple of additional points worth mentioning around the endpoint proxy functionality within AXIOM Cyber:
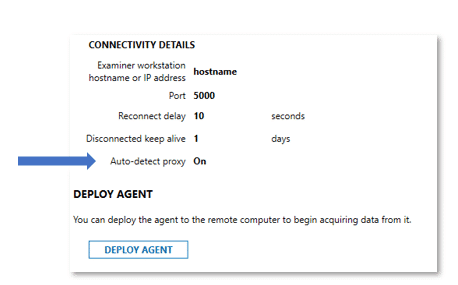
- Examiners who’ve previously created and deployed agents will need to recreate and deploy new agents with the proxy detection enabled. Customers can confirm this is enabled by selecting on Review Agent Details as seen in Figure 2 below.
2. Secondly, the agent needs to be run as a process (uncheck survive restart) for the local proxy detection to work.
The proxy functionality does not currently support proxy authentication, however as always if organizations run into any issues please don’t hesitate to reach out to our fantastic Support Team (support@magnetforensics.com) or to me directly at steve.gemperle@magnetforensics.com
About Steve Gemperle

Steve Gemperle was a Senior Special Agent with the United States Secret Service who specializes in cyber-crime. Steve joined the US Secret Service in 1999 and served with the US Secret Service until retiring in 2021. For the last decade of his career with the Secret Service he focused on computer crimes and served as Lab Director for the US Secret Service Southwest Regional Computer Forensic Lab. Steve has completed over 1900 forensic exams and 150 network intrusion investigations while working for the Secret Service.
Technical Advice Disclaimer
Magnet Forensics is dedicated to engaging with the DFIR community through our blogs and whitepapers. However, properly addressing technological issues often includes numerous variables that require independent assessment and strategies designed for each specific circumstance. Since Magnet Forensics cannot have complete insight into all variables involved in a specific situation, this blog/whitepaper is for informational purposes and should not be read as professional advice recommending techniques or technologies to address your specific situation. We do not accept responsibility for any omission, error, or inaccuracy in this blog/whitepaper or any action taken in reliance thereon.