
CUPS Artifact Support for macOS
What is CUPS?
It’s more than what holds my morning coffee! CUPS is an open-source printing system currently developed by Apple for use in macOS and other UNIX operating systems. CUPS utilizes the Internet Printing Protocol (IPP) to support printing to bother local and network printers. This system has been used by macOS since the 10.2 versions and higher.
For forensic examiners, CUPS often logs information into the system that can provide valuable data on what was printed, by who, and to what printer. As more and more modern printers use wireless technology, more are going to be treated as networked printers and these logs will only become more important in certain cases.
AXIOM and AXIOM Cyber has CUPS artifact support to parse out these log files and return information to examiner for quick review.
There are files spread into several areas for review when looking at CUPS information. First, there is the list of printers currently available to the machine which can be found in the data volume at the path: private/etc/cups/printers.conf.
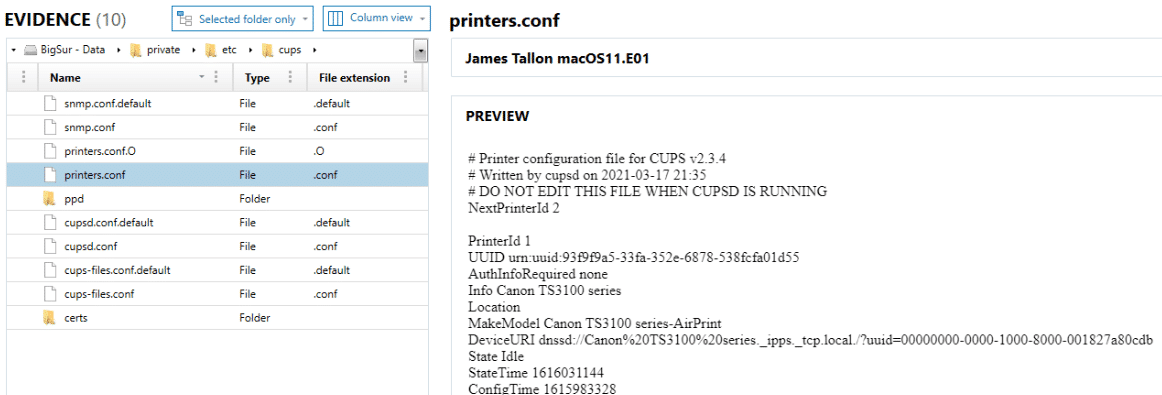
The data can also be reviewed at the path Library/Preferences/org.cups.printers.plist. This XML style plist file will store similar information:
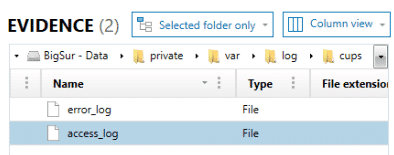
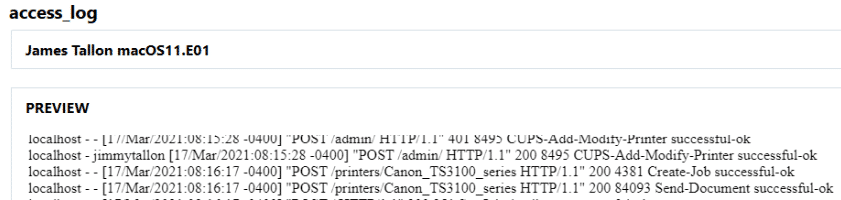
Now that we know what printers have been made available and within the access_log we can see that one of those printers received jobs, we might want to know what those jobs have been.
The next logs files are located in /private/var/spool/cups. These log files are not as easily read by the naked eye. Information stored within these “c#####” files can contain who printed the data, what was printed, when, and more.
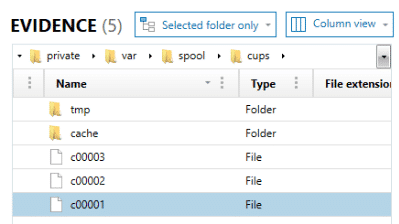
With the CUPS Print Jobs artifact, cached files are presented to the examiner in an easy-to-read format. Examiners can recover what file name was printed, the owner of the job, what application it was printed from, its format, Creation/Process/Completed times of the job (not the file), how many copies, and what printer actually received the job.
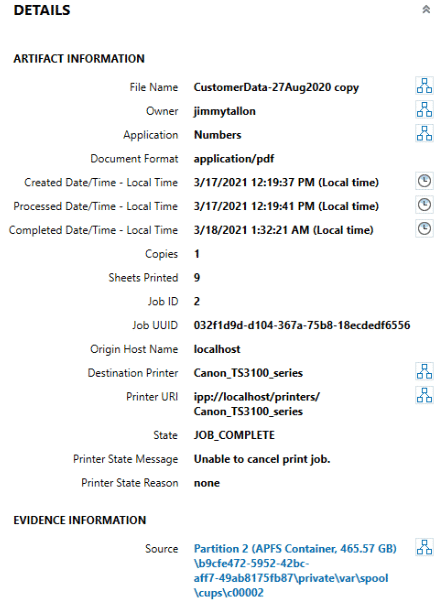
The original file that was printed may also be available for review within the “tmp” directory alongside these “C####” files. These files are named “D####” and the numbers will match the name of the file.
If the file is able to be rendered, it will display a “PREVIEW” card within the DETAILS pane. If the file matches a standard artifact format (picture or document), it can also be found within that appropriate artifact category.
By reviewing the above information, examiners may be able to track what files were printed, when, and the location or name of the printed that performed the job. This will enable them to further their investigations especially in cases where contraband or confidential files may have been sent to the printer.
Now where’s my coffee cup again?
Technical Advice Disclaimer
Magnet Forensics is dedicated to engaging with the DFIR community through our blogs and whitepapers. However, properly addressing technological issues often includes numerous variables that require independent assessment and strategies designed for each specific circumstance. Since Magnet Forensics cannot have complete insight into all variables involved in a specific situation, this blog/whitepaper is for informational purposes and should not be read as professional advice recommending techniques or technologies to address your specific situation. We do not accept responsibility for any omission, error, or inaccuracy in this blog/whitepaper or any action taken in reliance thereon.