
Could Digital Forensics be the Secret Weapon for Your Cybersecurity?
The Increasing Importance of DFIR
Digital forensics has become an indispensable part of cybersecurity programs. That’s largely driven by the harsh reality that falling victim to a security event isn’t a matter of if, but of when.
83% of organizations recently polled have experienced more than one data breach, making it clear that prevention alone isn’t sufficient protection.
To fully address security vulnerabilities, report on incidents, and mitigate the impact of future events, a comprehensive understanding of the root cause of the event is required. These important insights can only be acquired through digital forensic tools that provide an in-depth understanding of the incident by acquiring and analyzing data at a very granular level.
The unique insights and capabilities provided by a digital forensics tool offer a range of capabilities that can help businesses navigate the constantly evolving cyberthreat landscape:
Unravelling Increasingly Complex Threats
The sophistication and complexity of cyberthreats continues to evolve at a rapid pace, as the tactics and techniques used by external and internal bad actors become increasingly sophisticated. In our recent survey of DFIR professionals, 42% indicated that evolving cyberattack techniques present either an extreme or large problem for their investigations. Unravelling these complex threats by surfacing insights from more artifacts and from a variety of data sources can help reduce the damage and cost of an incident.
Developing a Complete Picture for Root Cause Analysis
With the right DFIR solution, examiners can gain a holistic view of incidents across the different platforms and tools used in corporate environments, including computers, mobile devices, SaaS solutions, cloud-based storage, and IoT devices. This detailed view of the incident facilitates identifying lateral movement and the root cause of incidents—which is crucial for containing the threat and strengthening security postures.
Protecting IP and Corporate Data
Digital forensics is a critical component of internal investigations, providing deep insights into potential malicious or accidental actions of internal teams and contractors, especially considering 43% of data breaches are caused by internal actors. To investigate the increasingly distributed workforce, DFIR solutions can provide the ability to remotely and covertly acquire detailed data from endpoints without tipping the subjects.
Complementing but Not Overlapping EDR
EDR and DFIR tools are complementary to each other, both playing a critical role in the incident response (IR) process. If we look at the relationship through the lens of the NIST Computer Security Incident Handling Guide, EDR tools fit best in the middle two steps-—providing real-time, continuous monitoring of suspicious incidents on endpoints as well as the ability to contain and respond to these incidents.
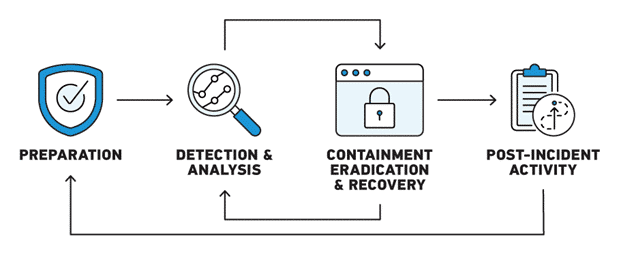
But EDR tools only provide limited insight into an incident, so DFIR tools are there to perform deep-dive analysis to ensure that remediation of security incidents is effective. If EDR answers the what and when of a security incident, DFIR answers the how and who, and may even get to the why in some cases.
Considerations for Your DFIR Lab
When establishing or upgrading a DFIR lab, the first item to determine will be the primary investigations that you will be conducting —which will, in turn, determine what types of evidence you will need to process so you can align your hardware and software with the range of devices and operating systems that you will need to investigate.
DFIR Lab Checklist
Software
Given the nature of this evidence, the majority of the requirements will be on the software solutions. The list below represents a starting point for your review of DFIR software but isn’t an exhaustive list. Your specific requirements and investigations will dictate the tools you require.
Typically, a digital forensics laboratory will have several digital forensics tools that can perform the same task to enable the lab to compare and validate investigation results.
Key consideration: With the depth of insights and range of data sources that DFIR solutions draw on, it’s important to ensure that a solution provides intuitive workflows to enable effective use of the platform for everyone from new to power-users.
The option to employ automation to mitigate the time required to perform manual or repetitive tasks can also help optimize the efficiency of DFIR lab resources and staff.
Collection of Data
- Ability to collect from required devices and operating systems:
- Endpoints
- Windows
- Mac
- Linux
- Cloud storage platforms and applications
- Mobile
- iOS
- Android
- SIM cards
- IoT devices
- Endpoints
- Remote collection from both on- and off-network endpoints
- Robust agent with flexible collection options
- Targeted and full collection capability to enable collections ranging from triage to full images
- Ability to collect data covertly
- Resuming collection when the connection is interrupted or lost
- Ability to collect Random Access Memory (RAM) and other volatile data
- Extensive artifact support for corporate software and services
- Frequency of updates—adding, maintaining, and updating data sources
- Support for images from other solutions
- Hash calculation and verification
- Data decryption capabilities
Analysis
- Combines evidence from different data sources into one case file
- Searching, sorting, and filtering capabilities to zero in on applicable evidence
- Leverages external sources to identify malicious files (internet security analyzers and databases, YARA rules, etc.)
- Interfaces tailored to the different evidence types (ex. email, Office documents, pictures and video, etc.)
- Facilitates quickly identifying relevant evidence, especially in large datasets
- Artificial intelligence
- Optical character recognition (OCR)
- Data visualization to help interpret data timelines and identify relationships
- Automation capabilities to streamline workflows and quickly surface case relevant evidence
- Robust tagging capabilities to incorporate input from other stakeholders
Reporting
- Customizable reporting options
- Variety of export format options (Excel, XML, HTML, PST, PDF, etc.)
- Format for sharing and collaborating on cases
- Load file support for eDiscovery
Complementary Software
Depending on the volume and variety of cases that your DFIR lab will be undertaking you may want to consider some additional software to manage cases and stakeholder involvement:
- Case management software
- Platform for involving stakeholders in the evidence or case review process
- Workflow Automation
To ensure your team is working as efficiently as possible, another important consideration is the vendor support options as well as training courses and certifications.
Hardware
To work efficiently, your DFIR lab will need a suitable number of dedicated forensic machines, or virtual machines, with enough power and bandwidth to match their function and team structure. Cloud hosting of software can also alleviate some of the requirements for physical locations and hardware.
- Interfaces and extraction tools to safely acquire data from different devices
- Imaging hardware —disk imagers
- Write blockers to ensure evidence isn’t accidentally altered and compromised.
- Forensic card reader
- Secure and accessible storage space (local and/or cloud instances)
- Secure internal network connection for collaboration and information sharing
- High-speed and secure internet connections to collect date from remote/off-network endpoints and cloud data sources
- Archival storage for long-term retention of cases
Transform Your Approach to Digital Investigations
Magnet Forensics offers a range of solutions tailored to the DFIR needs of corporate teams and service providers that simplify your investigations and help you get to the truth faster.
Explore our range of free tools, start a free trial of one of our enterprise solutions, or contact us at sales@magnetforensics.com.
Additional Resources
To learn more about establishing your DFIR lab, review the following resources which expand on the content and themes outlined in above: