
Best Practices for Ransomware and Data Extortion Memory Response
This is a post authored by Matt Suiche (Director, Memory, IR & R&D), and Ivan King (Security Research Engineer).
The Cybersecurity and Infrastructure Security Agency (CISA) & partners recently released a “#StopRansomware Guide” Cybersecurity Information Sheet (CSI) which aims at providing guidance to organizations to reduce the impact of ransomware incidents and a checklist of best practices for responding to these threats.
Among the recommendations, we noted several points regarding memory acquisition and analysis which we would like to expand on.
Fileless Attacks and Threat Hunting
One of the top recommendations provided by the guide includes: “Use security software to detect instances of RMM software only being loaded in memory.”
Threats actors often leverage memory focused techniques to evade detection and hide their presence such as Process Injection (T1055) where memory analysis is a key component for response and detection.
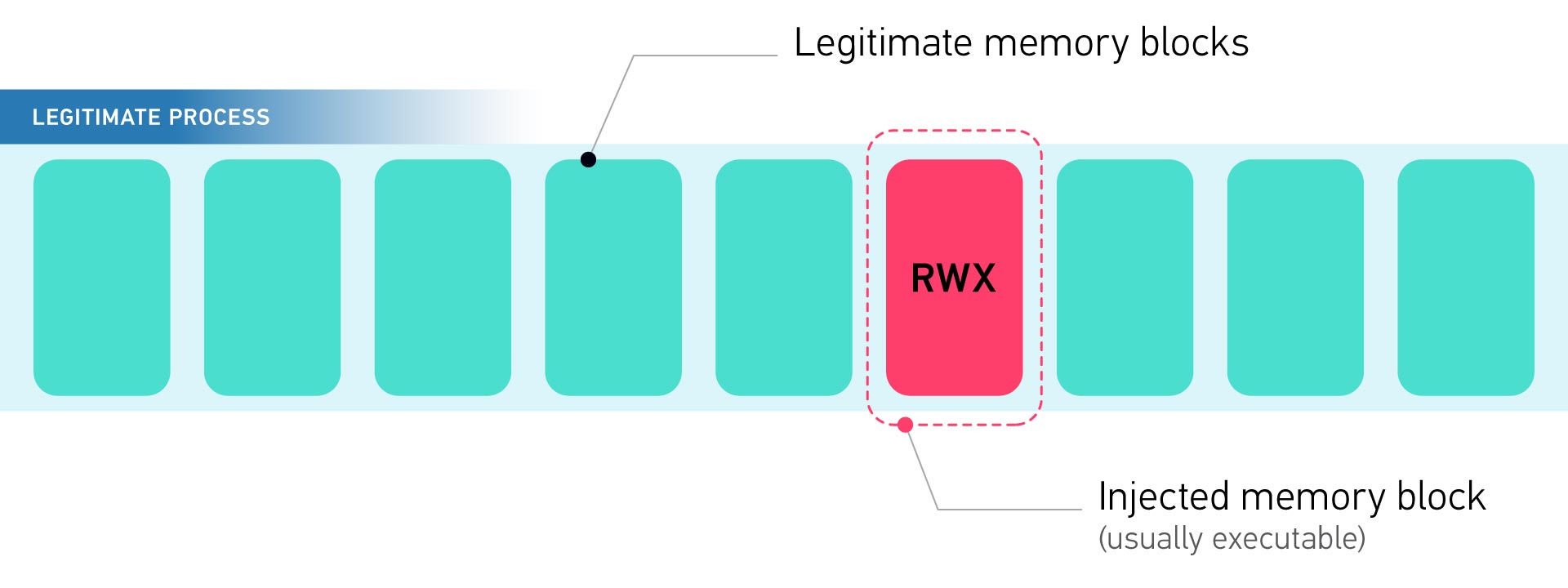
We agree that proactive memory threat hunting is a very important exercise, and in addition to XDR endpoint protections we recommend our customers leverage AXIOM Cyber for threat hunting as we described in our previous blogpost on hunting Russian intelligence malware “Snake”.
Capturing Memory Before It’s Gone
As part of the “Ransomware and Data Extortion Response Checklist”, the guide informs us:
- That powering down devices to prevent further spread of a ransomware infection will prevent your organization from maintaining artifacts stored in volatile memory which includes RAM images. This is a last resort step that should be conducted only if you cannot shut down the network or disconnect impacted machines from the network.
- We do encourage our customers to perform memory image acquisition before, especially for critical assets as it may contain critical evidence that will be relevant during the investigation phase.
- We also recommend our customers to use Microsoft crash dump as a file format for Windows as it is an interoperable format. You can read more about how acquisition best practice recommendations in our blogpost “Full Memory Crash Dumps vs. Raw Dumps: Which Is Best for Memory Analysis for Incident Response ? “
- Live memory (RAM) capture from systems with additional signs of compromise (use of exploit toolkits, malicious RDP activity, etc.) is also encouraged by the guide, in case your organization can share them with CISA, MSISAC with the relevant local, state, or federal law enforcement authority for extended identification or analysis if needed.
The Rise of Infostealers
Our threat intelligence team also noticed that several ransomware groups pivoted towards infostealing as an alternative strategy, you can read more about it in our previous blogpost about what are infostealers and how to investigate them.
Several infostealers we analyzed came with activity under the following MITRE ATT&CK groups:
| Tactic | Technique |
| TA00002 Execution | T1059 – Command and Scripting Interpreter T1204 – User Execution |
| TA00005 Defense Evasion | T1027 – Obfuscated Files or Information T1055 – Process Injection T1217 – System Binary Proxy Execution |
| TA0011 Command and Control | T1071 – Application Layer Protocol |
| TA0010 Exfiltration | T1041 – Exfiltration over C2 Channel |
For instance, one of the most popular ones, RedLine drops several further files upon execution which are then executed as child processes that spawn other legitimate operating system programs. This technique of obfuscating or encrypting the main infostealer capability is common among many infostealer families.
In this scenario, memory analysis enables the investigator to quickly:
- Identify suspicious processes by introspecting their memory.
- Identify C2 infrastructure via network connections from the suspicious process.
YARA rules can then be created that match on byte sequences inside the suspicious process that are then used to identify other infected machines.
An example YARA rule for the in-memory .NET assembly that it loads can be found here:
rule RedLine_dotNET {
meta:
description = "YARA rule for the in-memory .NET assembly"
author = "Ivan King (Magnet Forensics), Matt Suiche (Magnet Forensics)"
reference = "https://www.magnetforensics.com/blog/best-practices-for-ransomware-and-data-extortion-memory-response/"
strings:
$string1 = {31352e392e312e3232}
$string2 = {274e6972656f4e4f3120436f72706f726174696f6e20436f7079726967687420}
$string3 = {4e697274726f20435055}
condition:
all of them
}Deeper analysis of a memory image can even provide detection of novel threats and techniques.
Find Out More About Memory Analysis in AXIOM Cyber
To learn more about the recently updated memory analysis capabilities of AXIOM Cyber, check out Comae Memory Analysis Capabilities Integrated Into Magnet AXIOM Cyber. You can also learn more on using YARA rules in AXIOM Cyber here.
To try the memory analysis capabilities of Comae in AXIOM Cyber for yourself, update to the latest version over at the Customer Portal or request a free trial today!