
Forensic analysis of the Windows UserAssist artifact
What is the UserAssist artifact?
UserAssist is a feature in Windows that tracks the usage of executable files and applications launched by the user. It stores this information in the Windows Registry, which can be accessed by forensic analysts to reconstruct a timeline of application usage and user activity. Specifically, it is located within the NTUSER.DAT hive located at Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist. The entries within this artifact are ROT-13 encoded and Axiom automatically decodes these entries for quick review.
Over time, the UserAssist artifact has remained in the same location, but has slightly changed the information it contains. For Windows XP and Windows 2000, it stored application path, run count and last execution time. In Windows Vista and Windows 7, focus time was added, which captured how long the application was active. Windows 8 increased the granularity of the focus time, which gave greater detail to this data. Windows 10/11 added improved tracking for Universal Windows Platform (UWP) applications. These are applications downloaded from the Microsoft Store. For example, in this data restructuring you can now see detailed logging of USP app launches and track specific activities within the UWP app, which can provide greater specificity of the users actions.
Why is the UserAssist artifact important to your digital forensics investigation?
- The examination of UserAssist artifacts can be useful in:
- User Activity Reconstruction:
- By examining UserAssist entries, forensic analysts can determine which applications were used and when. This helps in reconstructing user actions and timelines of events on the system.
- Application Usage Patterns:
- The run count and timestamps provide insights into the frequency and recency of application usage, which can be critical in investigations.
- Corroborating Evidence:
- UserAssist data can corroborate other forensic evidence, such as file access times, browsing history, and log files, to build a comprehensive picture of user activity.
- Incident Response:
- In security incidents, understanding which applications were executed can help identify malicious activity, unauthorized access, or data exfiltration attempts.
Unlike prefetch files, UserAssist data will include information on whether an application was run from a shortcut (LNK file) or directly from the executable. This provides examiners with additional context around the execution of a program.
When examining UserAssist artifacts, Axiom parses the data in a format that is easy to read and understand, however certain key entries are:
RunPath
- This entry is encoded in ROT-13
- For example, this is a RunPath entry before decoding:
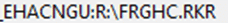
- Axiom decodes and presents in a readable format for you:
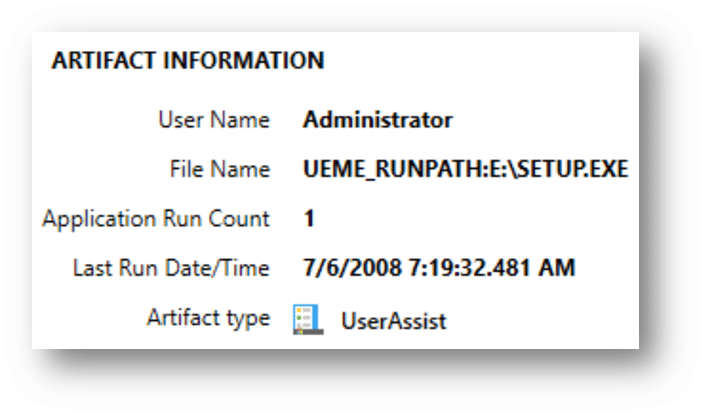
- By decoding these paths, analysts gain insights into user activities, application usage, and potential malicious behavior.
RunCPL (Control Panel Applets)
- These entries track the execution of Control Panel applets
- This would track if a user opened “system properties,” “add or remove hardware”, or “add or remove software”
- In this example, the user opened the “Automatic Updates” setting via the control panel.
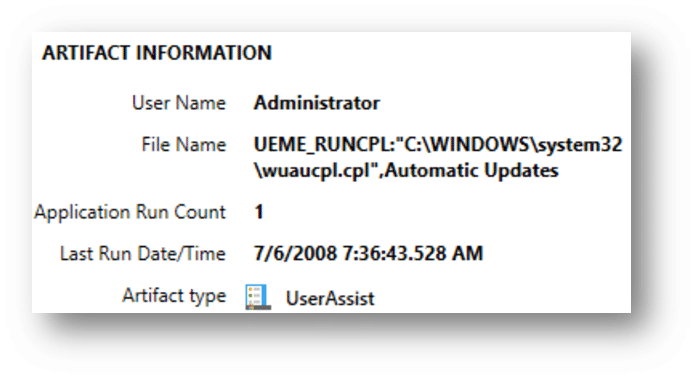
- This can be significant in understanding user behavior, system maintenance actions, and in correlating with other forensic evidence to reconstruct a comprehensive timeline of events during an investigation.
RunPIDL (Pointer to an Item Identifier List)
- RunPIDL entries track the execution of special folder items and shortcuts
- “Special folders” refer to predefined folders in the Windows operating system that serve specific functions and provide convenient access to common user and system resources. These folders are part of the Windows Shell namespace, which organizes and presents the file system and other objects to the user in a hierarchical manner.
- In this example, the user utilized the link to the wireless network setup wizard
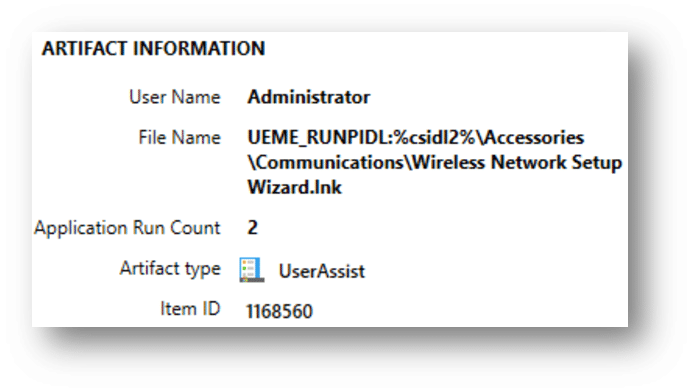
- Again, this information can assist in setting up user activities, which can be of significant forensic value.
The UserAssist artifact plays a pivotal role in digital forensics, offering a detailed log of user interactions with applications and system features on Windows operating systems. By capturing data such as application paths, run counts, and timestamps, UserAssist entries enable forensic analysts to reconstruct user activity with precision. This artifact aids in corroborating other forensic evidence, providing insights into user behavior, and identifying potential malicious actions. Its ability to track both traditional desktop applications and modern UWP apps makes it a comprehensive tool in the forensic toolkit. Axiom is able to locate and parse these artifacts for quick location and interpretation to assist you with any type of investigation.