
Digital Forensics: Artifact Profile – USB Devices

Importance to Investigators
USB device history is an invaluable source of evidence in digital forensics, playing a crucial role in various investigative scenarios. When an examiner needs to determine if an external device was connected to a system, USB artifacts provide definitive traces of such activities. This evidence can reveal not only the connection but also the specific details of the devices involved, such as serial numbers, manufacturer information, and timestamps of connection and disconnection events. This level of detail can be pivotal in constructing timelines and understanding user behavior on the system.
Additionally, analyzing USB device history allows investigators to understand the usage patterns of USB devices on a given system. This includes identifying the types of devices connected, the frequency and duration of their use, and any data transfer activities that took place. Such information can shed light on whether a device was used for legitimate purposes or if it was involved in unauthorized or malicious activities.
In cases where a suspect is believed to have used a USB device in the commission of a crime or incident, USB artifacts can provide critical evidence. For instance, if sensitive data was exfiltrated from a system, USB device logs can reveal the presence of storage devices that might have been used to copy the data. Similarly, if malware was introduced via a USB device, the history of connected devices can help trace the source of the infection. The significance of USB device history extends to both criminal and civil investigations. It can help in cases of intellectual property theft, insider threats, and compliance violations in corporate environments.
Location of USB artifacts:
The majority of USB-related artifacts are located within the Windows Registry
Windows XP:
Registry Key: USB-related information is stored in:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\USB\
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\USBSTOR\
SetupAPI Logs: C:\WINDOWS\setupapi.log
Windows 7 had a few changes:
SetupAPI Logs moved to: C:\WINDOWS\INF\setupapi.dev.log
The category Windows Portable Devices was added: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Portable Devices\Devices
Windows 8/8.1 added:
DeviceClasses: Additional device information may be found under:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\DeviceClasses
Windows 10 and Windows 11:
The category Device Container ID was added:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\usbccgp
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\usbhub
Additional USB artifacts can be located:
Windows Event Logs:
- System event logs may contain entries related to USB device insertions and removals.
- Event Viewer path: Applications and Services Logs\Microsoft\Windows\DriverFrameworks-UserMode\Operational
Windows Prefetch:
- USB-related executables may be found in C:\Windows\Prefetch\.
Mounted Devices:
- Mounted device artifacts: HKEY_LOCAL_MACHINE\SYSTEM\MountedDevices
UserAssist:
- Tracks user interaction with USB devices in HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist.
That all sounds very complicated, and information must be pulled from several locations to get a complete picture of the USB device history. Fortunately, Axiom parses this information and presents it to the investigator/examiner in a quick, easy-to-understand format. Let’s look at a couple of examples of what this looks like and what information is stored in each location.
In Axiom, we see:
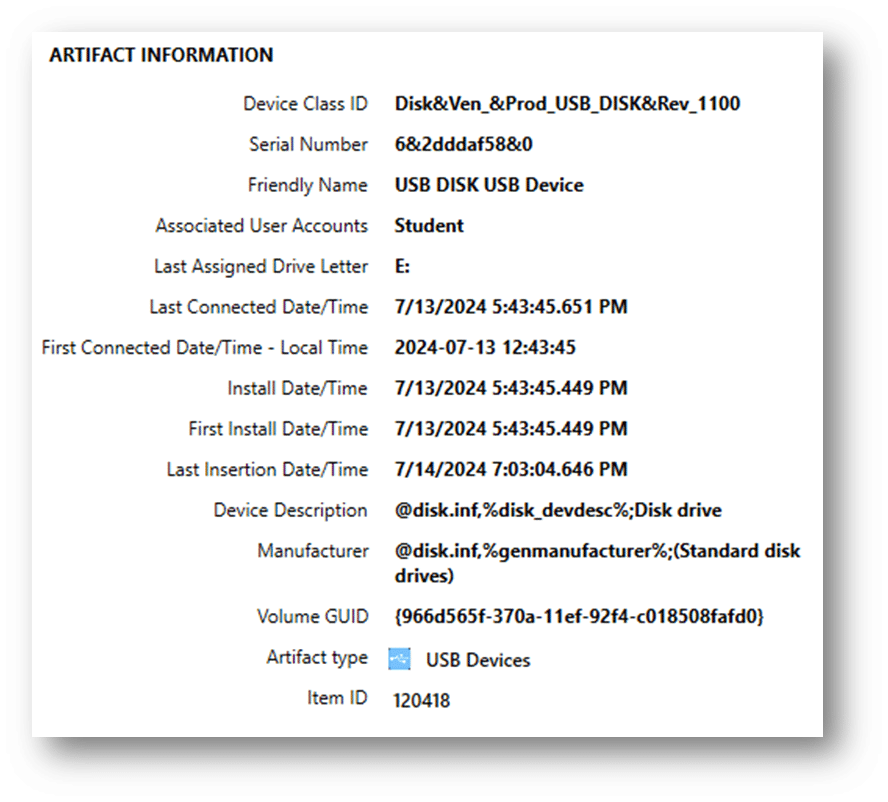
From this information, we can see critical information about the USB device, including the last assigned drive letter. However, let’s take a look at the Windows Registry to see where this information is directly pulled.
USBSTOR:
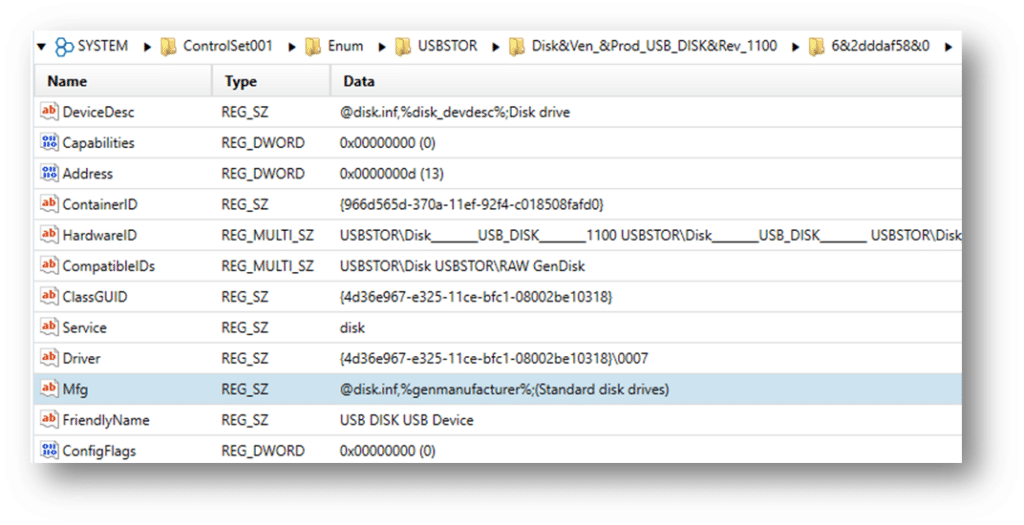
Also, in USBSTOR, you can see the last inserted date:
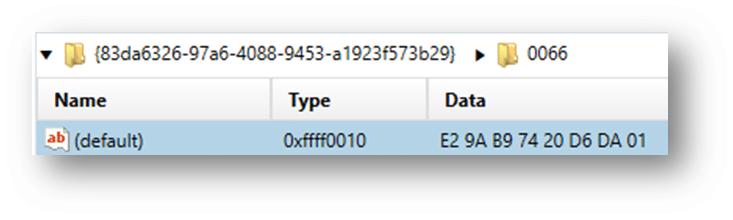
This date/timestamp is stored in the Windows Filetime (UTC) format and must be converted (Axiom converts these timestamps for you). The first connected date/time for this device will also be stored in the same format.
From the MountedDevices key, we can see where the mapped drive letter:
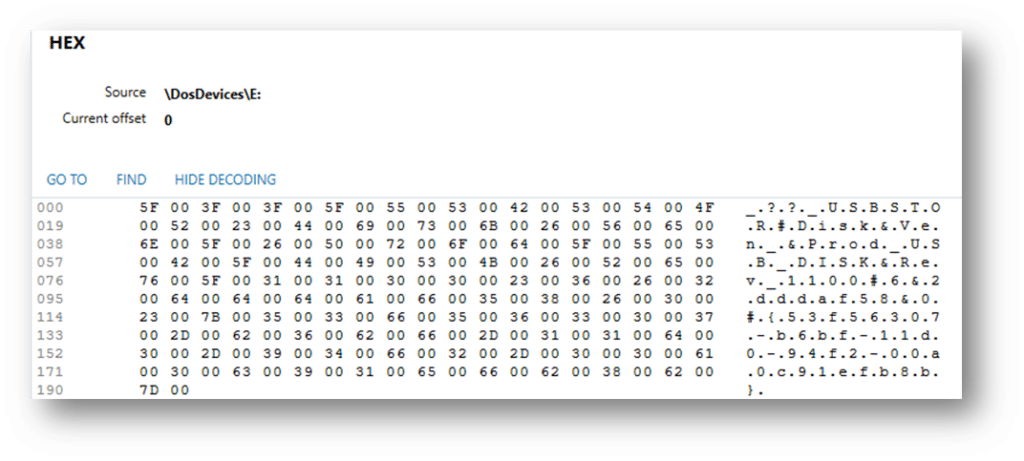
The Serial Number of the USB device is seen here and connects our inserted device to the mapped drive “E:”
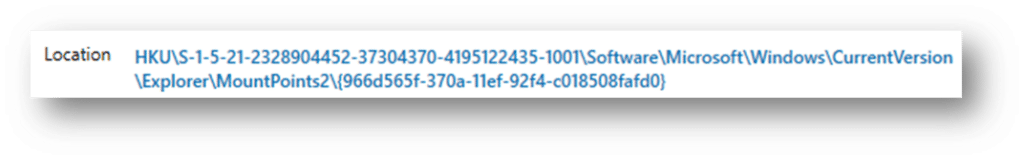
The MountPoints2 key will reveal which user was logged in and active when the USB device was connected. MountPoints2 lists all of the device GUIDs that a particular user connected, so you may need to search through each NTUSER.dat hive on the system to identify which user connected a specific device. In this case, we can see it was located in the NTUSER.DAT registry hive for the user “Student”:
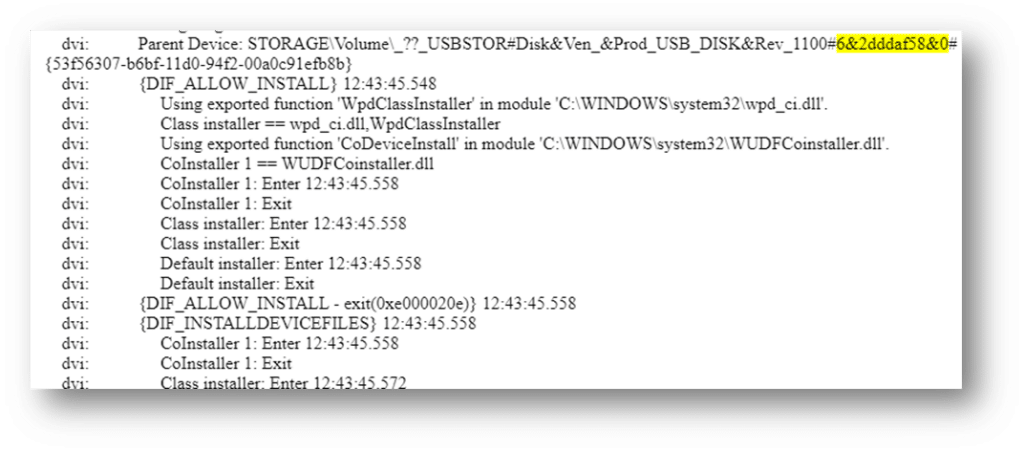
Examiners can also identify when the device was first connected to the system (in local time) by searching for the serial number in the setupapi log. Unlike the other timestamps mentioned (which are stored in UTC), the setupapi log stores data in the system’s local time and therefore must be converted before performing a timeline analysis.
UserAssist:
The UserAssist artifact is a valuable resource in digital forensics for analyzing user activity on a Windows operating system. It is part of the Windows Registry, specifically located in the following Registry paths:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{GUID} (where GUID is a globally unique identifier)
Here is an example of where UserAssist can help in USB drive-related investigations:
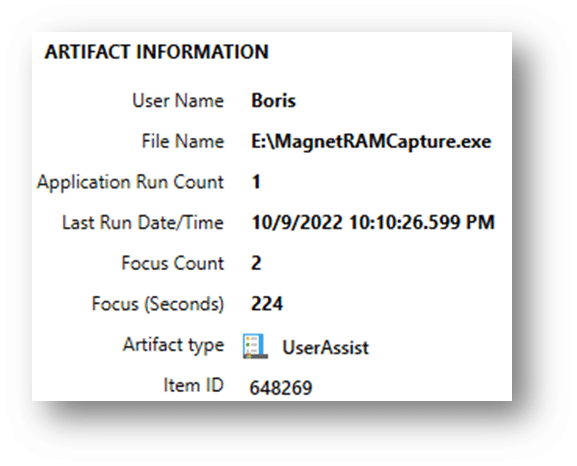
Here we can see the user “Boris” launched the MagnetRAMCapture.exe from the “E” drive, which was a removable USB device at the time. For more information on this artifact, please visit https://www.magnetforensics.com/blog/artifact-profile-userassist/.
The process of gathering USB device history from various registry locations and logs can be intricate and time-consuming. However, tools like Magnet Axiom significantly simplify this task. Axiom is designed to parse and present USB-related data efficiently, providing investigators with a clear, comprehensive view of all relevant artifacts. This tool consolidates information from multiple registry keys and logs, converting timestamps and mapping drive letters automatically, which accelerates the analysis process. By presenting critical information, such as device serial numbers, connection timestamps, and user interactions, in an easy-to-understand format, Axiom enhances the speed and accuracy of forensic investigations. This streamlined approach allows examiners to quickly determine the usage patterns of USB devices, trace data transfers, and identify potential malicious activities, thereby facilitating faster and more effective forensic analysis.
Get Magnet Axiom today!
We continually improve Axiom to make it our most comprehensive digital forensic platform. When every second counts, it’s important that we do what we can to streamline the primary workflow of examiners.
If you’re already using Axiom, download the newest version of Axiom at the Customer Portal. To try Axiom for yourself, request a free trial today! If your agency needs to perform remote collections, collect from cloud storage services, or Microsoft Office 365, check out what’s new in Axiom Cyber here.