10 Ways Magnet Forensics Supports eDiscovery
Magnet Forensics was proud to recently be named by IDC as a Major Player in the IDC MarketScape: Worldwide eDiscovery Early Case Assessment Software 2022 Vendor Assessment (doc #US48970222, September 2022).
But what does it mean to be named a Major Player?
Simply put, the IDC MarketScape positioned Magnet Forensics as a Major Player based on strategy and capabilities. After rigorous reviews, they found characteristics that meet current market demands and expected buyer needs when it comes to offering eDiscovery early case assessment.
What are some of those characteristics? We’ve collected 10 to summarize just how Magnet Forensics supports eDiscovery, so, without further ado, here we go!
1. Cull the Noise
One of the most time-consuming and expensive parts of eDiscovery is collecting the right amount of information. Collect too much and teams will waste hours sifting through irrelevant data. Collect too little and key evidence could be missed.
Ryan O’Leary, Research Manager, Privacy and Legal Technology, IDC, and author of the IDC MarketScape
Magnet Forensics exhibits strength in the extensibility of their tools to collect most types of data and cull the noise.
Magnet AXIOM Cyber solves this challenge at the point of collection by giving analysts the ability to be targeted about their collections and only collect what they need as a part of their discovery. Use AXIOM Cyber to create custom targeted locations on an endpoint. For example, if you know that the data you’re looking for is a result of data that was downloaded, be targeted about that collection and collect “Downloaded Items”.
By being targeted about collections, you’re culling the noise before it even begins.
2. Easy Handoff to Review Platforms
Once data has been collected and culled, it has to go through a review process. AXIOM Cyber can do an excellent job collecting and culling as well as providing an initial analysis, but it needs to ultimately be reviewed—in a platform like Relativity for example.
AXIOM Cyber makes that handoff of culled and collected data to review easy with load files.
Use AXIOM Cyber to create a load file that can be ingested by eDiscovery review tools. Load files generated by AXIOM Cyber include:
- A plain text delimited file with a .dat extension in the Concordance/Relativity format containing metadata for the included artifacts
- Folders with accompanying natives and text including:
- MSG file for email
- HTML chat threads for chat messages from Slack or other chat-based communication services
- Original files for documents, media, and other file-based artifacts
3. Collect Data From Almost Any Source
Gone are the days when evidence for discovery was primarily in email and documents. Now evidence is on mobile devices in the form of text messages and other messaging apps. It’s in cloud-based services like Slack and Microsoft Teams, or cloud-based storage services like Microsoft Azure or AWS.
Having one collection tool that can collect from computer, mobile, and cloud sources simplifies and speeds up the collection process while streamlining the output.
Magnet Forensics has the capability to collect virtually any data source across virtually any environment or device.
IDC MarketScape: Worldwide eDiscovery Early Case Assessment Software 2022 Vendor Assessment
AXIOM Cyber is that one collection tool that get evidence from computer (Mac, Windows, and Linux), mobile device, and cloud sources like Slack, Office 365, Google Workspace, AWS and Azure, and so much more.
Check out our on-demand webinar, Dig Deeper: Cloud Investigations with AXIOM Cyber, to see how easy it is collect from Office 365 and Slack.
4. Support for the Hybrid Workforce
Now that many employees are working from home and most likely not connected to the corporate network via VPN, collection of data from those endpoints can be extremely challenging.
You not only need a tool that can perform remote collections, you also need a tool that can perform remote collections of endpoints when they are off-network (i.e. not connected to the corporate network). And it needs to be done reliably.
Use AXIOM Cyber to perform remote collections including endpoints that are off-network.
5. Depth of Artifacts
It’s not only the breadth of evidence data sources and artifacts that is a strength of AXIOM Cyber, it’s also the depth of artifact support.
The depth that Magnet Forensics can explore the data and artifacts is hard to compete with.
The IDC MarketScape: Worldwide eDiscovery Early Case Assessment Software 2022 Vendor Assessment
Magnet Forensics got its start supporting law enforcement agencies with criminal investigations such as child exploitation, human trafficking, and other violent crimes. The digital evidence used for these types of investigations must be unassailable, therefore the data collected for artifacts must be equally unassailable. The same technology and approach used for our public safety customers is the same technology and approach that is used for eDiscovery.
6. Scan Multiple Endpoints at Once
When beginning the discovery process, sometimes it’s important to know if there are other endpoints that need to be included in the case. Let’s say, for a hypothetical example, Sven is a Sales rep and he has downloaded a confidential customer list that he wasn’t supposed to. The initial discovery includes Sven’s devices and accounts, however what if Sven shared the file with a colleague on his team? The scope of the discovery could expand to include other devices and accounts.
Magnet AUTOMATE Enterprise is an automation solution purpose-built for enterprises to concurrently collect and process evidence from multiple targets and data sources while integrating with other tools to orchestrate workflows with minimal downtime and human interaction.
By leveraging the automation power of AUTOMATE Enterprise, the analyst working Sven’s case could have a preset playbook or workflow designed to collect data relevant to eDiscovery and simply enter the information of all the endpoints that need to be collected from. From there, all that data can be ingested by AXIOM Cyber and the analyst working the case can scan endpoints of Sven’s immediate team, for example, and then search for the file name of the confidential customer list to see if it shows up where it shouldn’t.
7. Analyze Email With Ease
Email is a large component of many eDiscovery cases. When analyzing emails, it’s important to get through this work swiftly and efficiently. AXIOM Cyber’s Email Explorer view helps analysts manage emails by presenting them in an intuitive and familiar format that mirrors the appearance of common email platforms, such as Microsoft Outlook.
Recognizing that reviewing email evidence is especially important for eDiscovery investigations, we have also added the ability to easily select and export multiple records for legal stakeholders.
8. Time Filtering
One of the easiest ways to ensure analysts are using their time wisely is to cull privileged and other non-relevant data. A simple yet powerful feature of AXIOM Cyber is the time filtering capabilities.
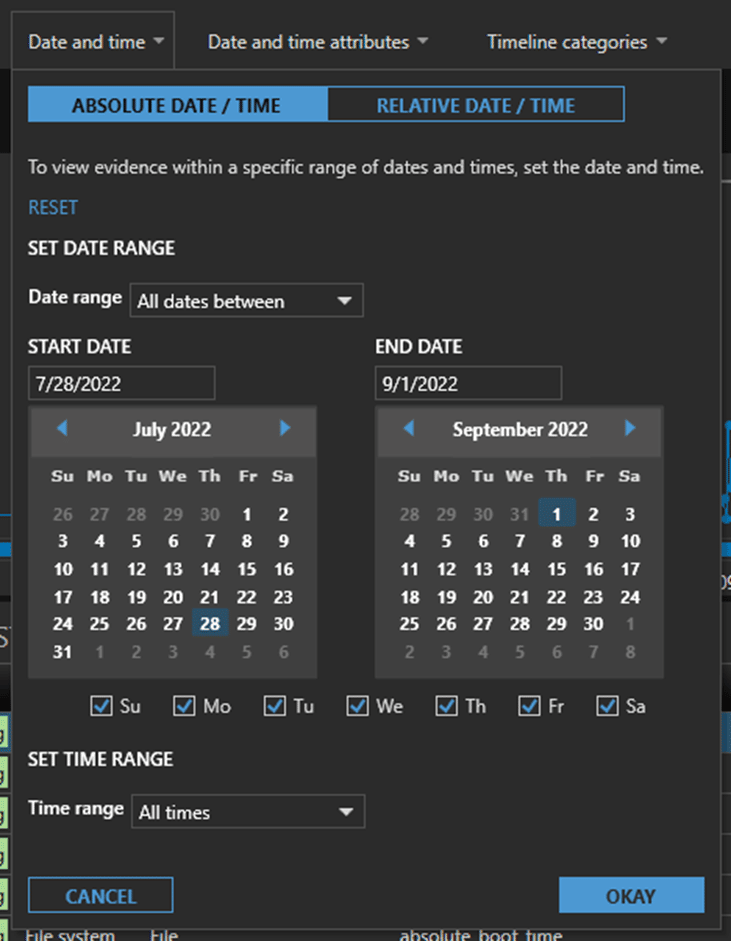
Absolute Time Filters
Absolute Time filters let analysts choose a date and time range with options for “All dates before”, “All dates after”, “All dates between”, and more. Remember Sven? Let’s say we’re working his case and our discovery is only limited to July 28 to September 1. Using AXIOM Cyber, analysts can be explicitly clear about the boundaries of their search including all dates before, all dates after, or to really narrow in on a time, use all dates between.
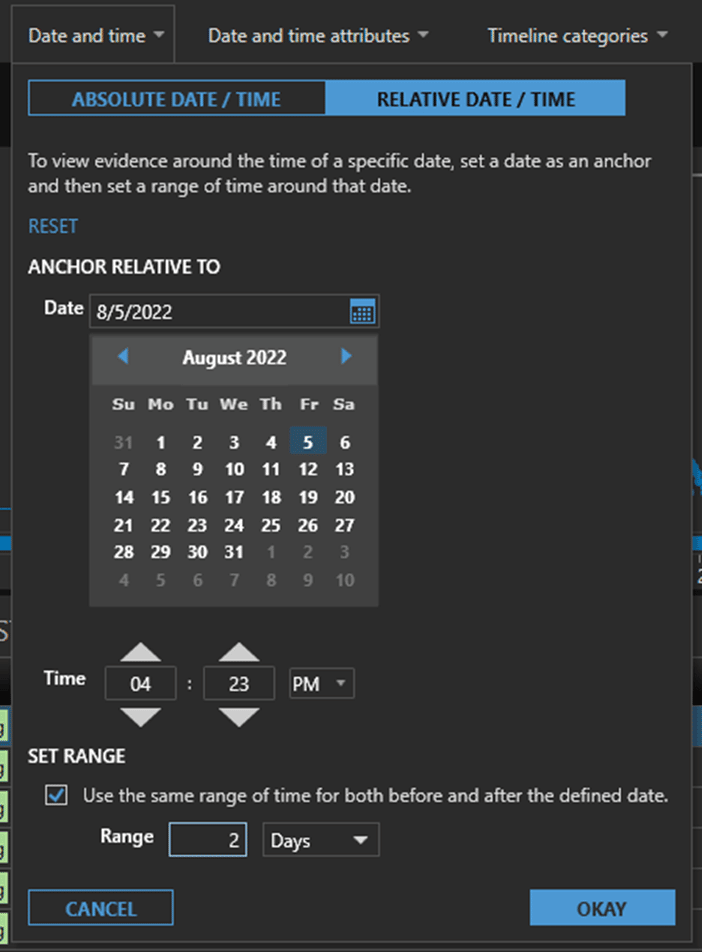
Relative Time Filters
Relative Time filters are useful when it’s known what time an action or event has happened. If we know that Sven downloaded the confidential contact list at 4:23pm on August 5, we can filter evidence for two days for example before and after that event to see what else Sven was doing. Did he send it to someone else? Did he copy it to external storage? Did he save it to Dropbox? All of these questions can be answered using Relative Time filtering.
9. Create a Timeline
Once an analyst has narrowed down their evidence using time filters, it’s easy to build a Timeline of events with AXIOM Cyber which can be very helpful to further explore what else has happened and how.
10. Tag Evidence
eDiscovery analysts don’t work in a silo. They are collaborating with many other stakeholders both internal and external. A useful way to facilitate that collaboration is through tagging or labelling evidence.
AXIOM Cyber enables analysts to tag almost any piece of evidence found and tags can then be shared in load files. Once that load file is ingested by Relativity for example, those tagged pieces of evidence will be ready for review.
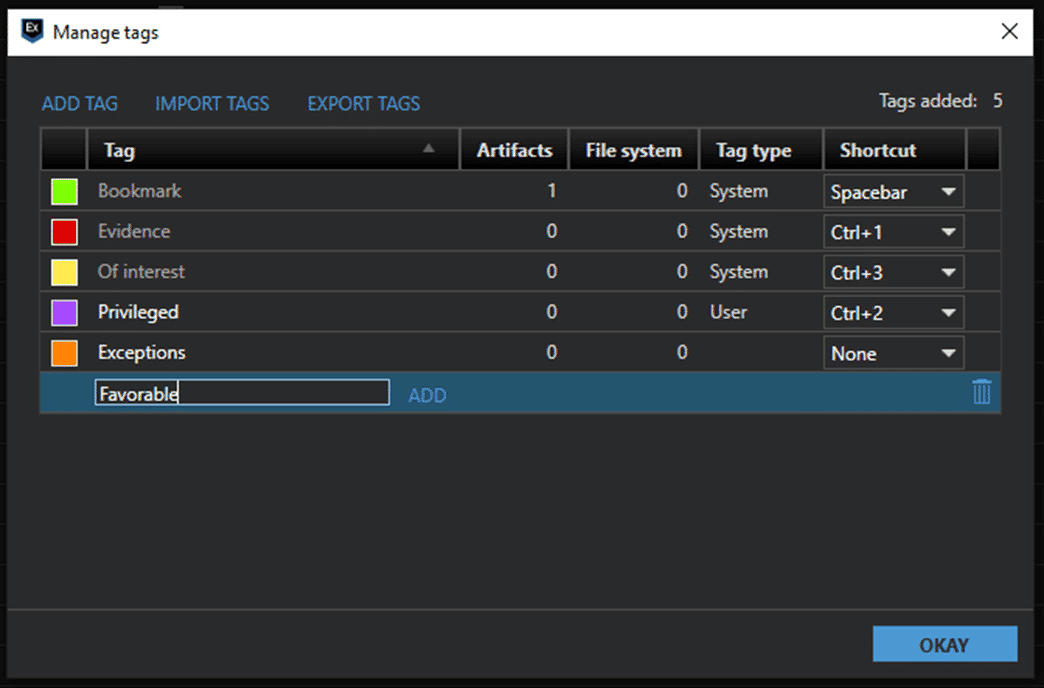
AXIOM Cyber’s Tag Manager also provides the flexibility to support whatever kind of tag or label naming convention is most familiar to you. Create new tags, color code them however you like for consistency, and more to streamline tagging and collaboration.
Try Magnet AXIOM Cyber Today
If you are supporting eDiscovery investigations and looking for a better way to perform targeted collections from virtually any data source, perform early case assessment and then handoff that work as a load file for later review including tagged material, then try Magnet AXIOM Cyber today.